Interset – formed in 2015 and acquired by Micro Focus in 2019 - enables security operations centre (SOC) teams to solve the complex problem of detecting sophisticated attacks, such as insider threats, through the use of behavioural analytics. Interset is trusted to protect critical data in some of the world’s largest organisations in the finance, critical infrastructure, high-tech manufacturing, healthcare, utility, and energy industries.
Interset’s user and entity behavioral analytics (UEBA) provides security teams a new lens to find and respond to unknown threats before data is stolen. Powered by unsupervised machine learning, Interset measures the unique digital fingerprint of systems and users, distilling billions of events into a handful of prioritised threat leads. Interset’s machine learning models, combined with a highly intuitive user interface (UI), accelerates threat detection and investigation from weeks to minutes.
UEBA is a category of security products initially defined by Gartner back in 2015, although the E was added a year later and mainly takes into account the growth of IoT devices, which can also pose a threat. UEBA products such as Interset take event monitoring data and looks for anomalous trends and events as compared to ‘standard’ behaviour. So the download of multiple files from a server to the same address may trigger an alert, for example.
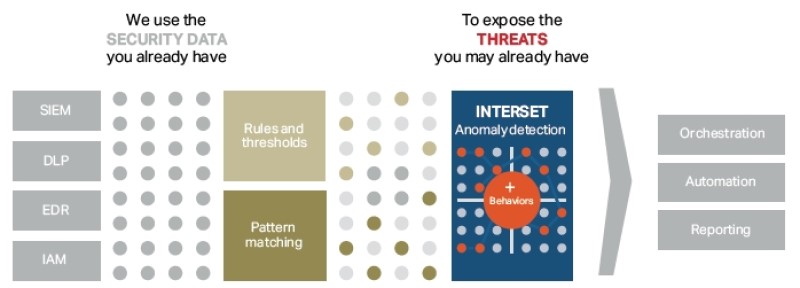
Interset UEBA views existing security data – as collected by a SIEM application such as Micro Focus ArcSight - through a new lens in order to identify hidden threats by looking for anomalous behaviour. This produces high-quality threat leads, allowing security teams to respond and remediate quickly and effectively, as shown in figure 1.
Unsupervised Artificial Intelligence
Interset (as do most other UEBA products) uses artificial intelligence and machine learning techniques. What makes Interset stand apart from other offerings is its use of ‘Unsupervised Machine Learning’. Other ‘supervised’ techniques rely on labels in the data to identify threats. A simplistic example is how to distinguish between a group of cats and dogs. Supervised machine learning relies on each cat or dog being labelled as one or the other. Unsupervised techniques look for attributes of dogs (e.g. they bark) and cats (e.g. they meiow) to separate the groups. Unsupervised machine learning is a more powerful and flexible technique.
Unsupervised machine learning finds new patterns in large sets of data, no matter how random that data seems. The algorithms collect data and cluster it to find structures and recognize emerging patterns. This type of machine learning is particularly well-suited to insider threat detection because inside(r) threat scenarios typically deal with limited, label-ess datasets.
Interset’s analytics platform is built from the ground up to execute unsupervised machine learning algorithms at enormous scale using an Apache Hadoop compute architecture (will Vertica be an option in future?). These algorithms extract the available entities (individual users, machines, IP addresses, web servers, printers, etc.) from log files and observe events that relate to these entities to determine what is normal or expected behaviour. As new information comes through the analytics process, it is evaluated against previously observed behaviour, as well as dynamically measured statistical peer groups, to assess potential risk.
When it comes to threats, every entity—person, machine, device, etc.—has a ‘unique normal’. It also follows that each entity’s interaction with another entity is also unique with its own normal set of behaviours. No two threats are the same, making detection of such threats exceedingly difficult. Accurate threat detection requires precise measurement of how a unique entity behaves. This baseline of unique normal can then be compared with itself to see aberrations. Rules and thresholds don’t work because they assume the same rules work for every entity, creating many false positives. A solution needs to reduce false positives, which is achieved through an architecture that can scale horizontally to accommodate the measurement of unique normal for thousands of entities.
Baselines and Risk Scores
Interset creates unique behavioural baselines for every entity and its relationship to every other entity by applying unsupervised machine learning to mathematically discover patterns. The ability to dynamically, mathematically identify unique baselines for peer groups further reduces false positives.
Interset scales horizontally to accommodate measurement of unique normal for millions of entities, and the platform comes with hundreds of built-in analytical models that automatically incorporate “live” data. This automated data analysis, powered by machine learning, enables flexible and effective threat detection as it removes the traditional dependency on rigid rules and thresholds based systems, which generate many false positives and requires continuous, labour-intensive maintenance.
Interset leverages machine learning to measure both event risk and entity risk. This is important because one entity (e.g., a user) can participate in multiple anomalous events (e.g., authentication, access time, data movement). For example, a single erroneous authentication attempt is suspicious but not alarming.
Next, Interset’s threat detection creates a meaningful risk score by compressing all of the various anomaly probabilities into a single entity risk score, essentially normalising each single entity risk score against each other. This gives security practitioners a meaningful, rank-stacked list of threat leads out of millions of entities continuously measured over time.
Interset’s UEBA leverages more than 450 machine learning models to baseline the behaviour of every user and entity within an organisation and evaluate deviations from those baselines as potentially risky behaviours. The machine learning models are carefully mapped to ATT&CK’s 219 techniques* to better understand:
- Which attack techniques customers face most often
- Where Interset provides coverage most effectively
- How to leverage our anomaly models to protect businesses against real threats.
NB. MITRE’s ATT&CK (Adversarial Tactics, Techniques, and Common Knowledge) framework is a living knowledge base of threat tactics and techniques observed in real-world attacks on enterprise networks, and it plays a pivotal role in Interset’s user and entity behavioural analytics. With detailed information on data sources, mitigation, examples, and detection for many tactics and techniques, ATT&CK is a one-stop shop for security researchers, practitioners, or vendors to better understand how to effectively protect organisations from real attacks. Today, Interset’s UEBA covers 75% of the ATT&CK framework that has been seen in the wild, and coverage continues to grow.
To create accurate risk scores, Interset’s analytics engine utilises methods that include probabilistic methods for uncertain reasoning, clustering algorithms, classifiers and statistical learning methods, and neural networks. It also employs a statistical approach to compress all of the various anomaly probabilities into a single entity risk score, a critical aspect of meaningful, actionable security analytics. A score is computed for each event to quantify the anomalies. Interset aggregates these event probabilities to their associated entities, taking into account the entities’ previous risk scores and outside intelligence that can affect the entity, such as employee watch lists, threat intelligence, and data from other security tools. This produces a risk score that considers all entities related to an event based on all the context Interset can gather.
As the analytics engine refines anomaly patterns, it learns which users create more risk, which files are the most at risk, and which machines are most often part of risky activities. Through statistical analysis, the engine also quantifies just how anomalous an observed behaviour is. The more an entity is involved in high-risk anomalous activities, the more its risk score increases. Conversely, a risk score will decrease over time for an entity that is not involved in high-risk activities, but instead behaves normally compared to itself and other similar entities.
This risk scoring is calculated for every single entity—every single user, machine, IP Address, printer, web server, fileshare, etc. From these millions of individualised risk scores, the machine learning normalises them so that they can all be compared with each other accurately, creating a single rank-stacked list of threat leads for security teams to prioritise time and effort.
Architecture
Interset runs on Linux: Centos 7.6 and Red Hat 7.6 are supported. A number of other open source packages must be installed and configured to support the Interset analytics engine. Apart from Hadoop, then Elasticsearch, Kibana, Kafka, Nifi, Storm and Zookeeper amongst others are required. Oracle OpenJDK must also be installed.
The software is installed across a number of active nodes:
- Monitoring node ( where Ambari or Cloudera Manager is installed)
- Master node(s)
- Stream node(s)
- Compute node(s)
- Search node(s)
- Reporting node
Interset is multi-tenanted by default.
Dashboards, Reporting and User Interface
With more accurate and automated targeted attack and insider threat detection, SOC analysts can focus their time on investigating the threats that matter most, via an intuitive user interface (UI) and comprehensive API. Dashboards (see figure 3 for an example), timelines, filtering, and search capabilities enable analysts to quickly refine data and logs down to the most relevant information.
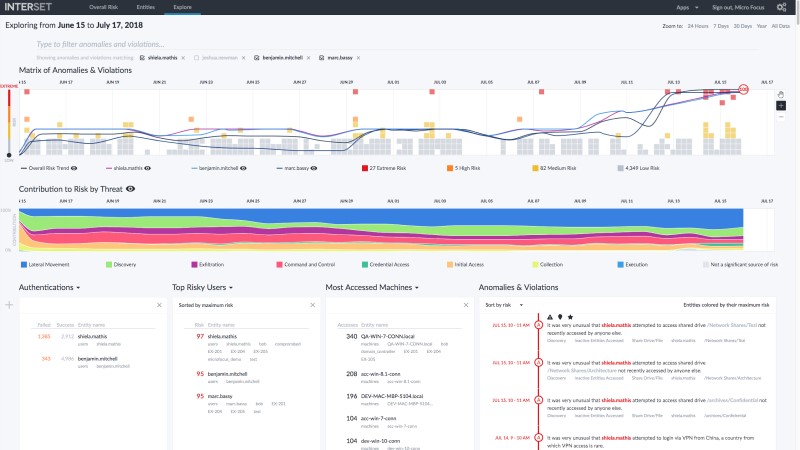
Response time is critical for data breaches. Interset’s threat detection software enables intuitive, contextualized detection and investigation and enables SOC teams to initiate actions quickly via security orchestration and automation response (SOAR) solutions to begin remediation. Interset UEBA also provides downloadable reports that summarize immediate risks.
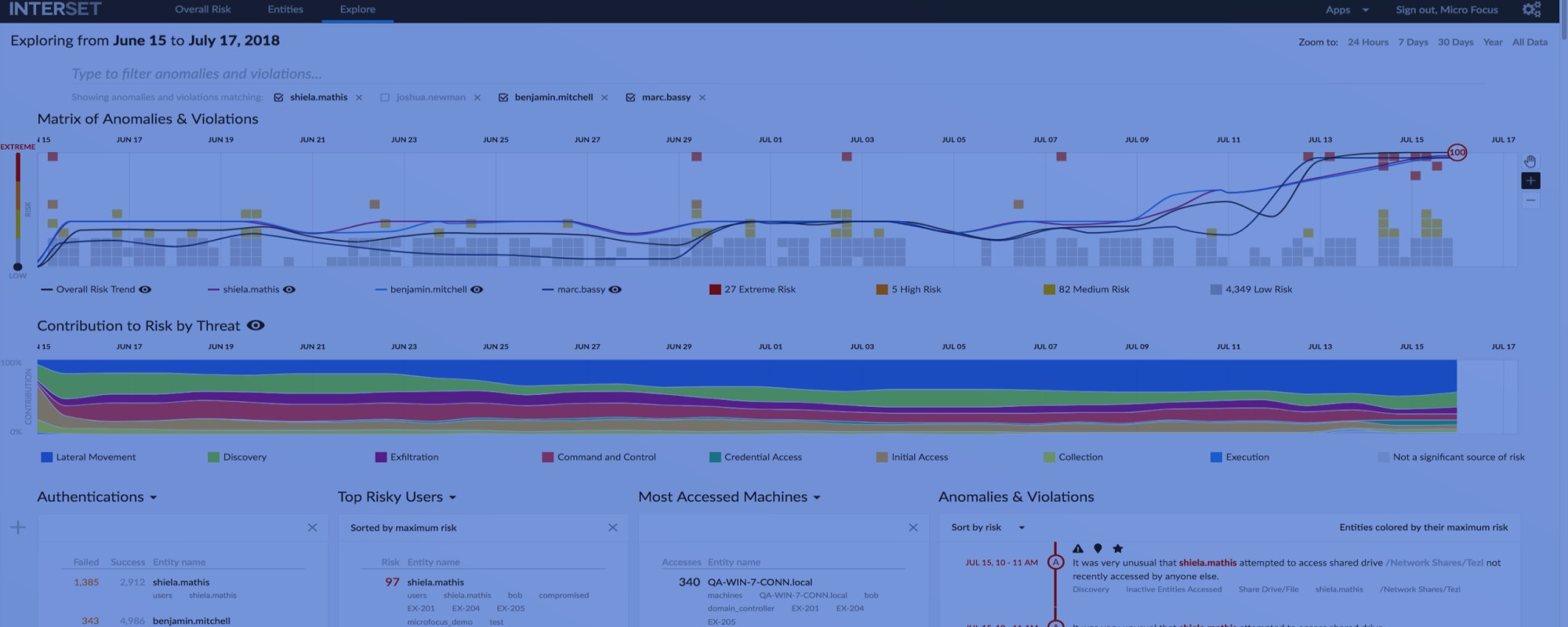
When you first log into Interset, you are taken to the Overall Risk page.
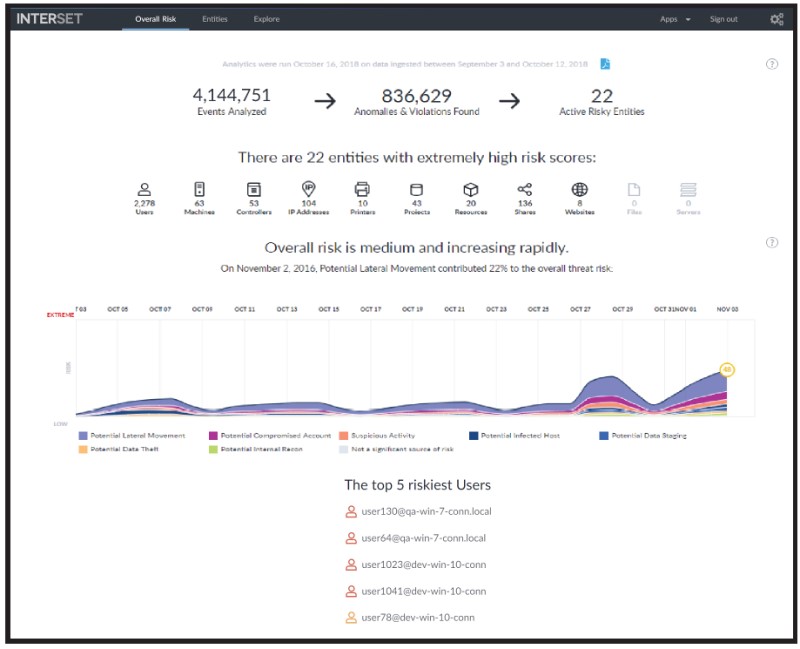
This page allows you to see, at a glance, the overall risk status of your organisation. For example, in the screenshot below (Figure 4), you immediately see:
- just over 4 million events were analysed
- about 836 thousand anomalies and violations were found
- 22 active risky entities were identified
- the overall risk is medium and increasing rapidly
- the threat of Potential Lateral Movement is contributing 22% to the overall risk
- the various streams of the graph indicate the potential threat types involved
- the types of entities involved and their risk counts
- the top five risky users
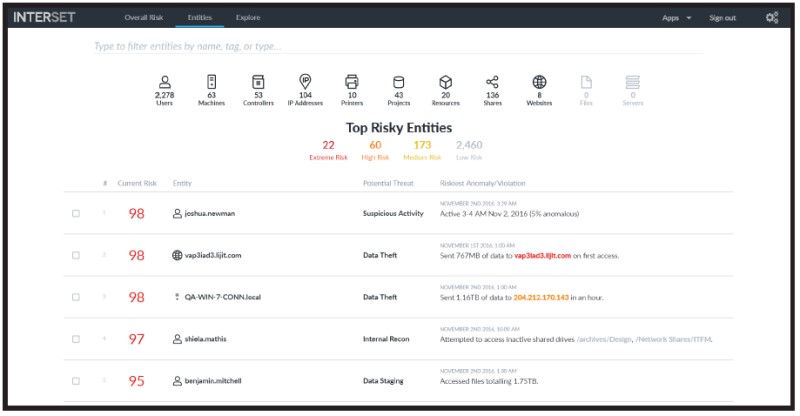
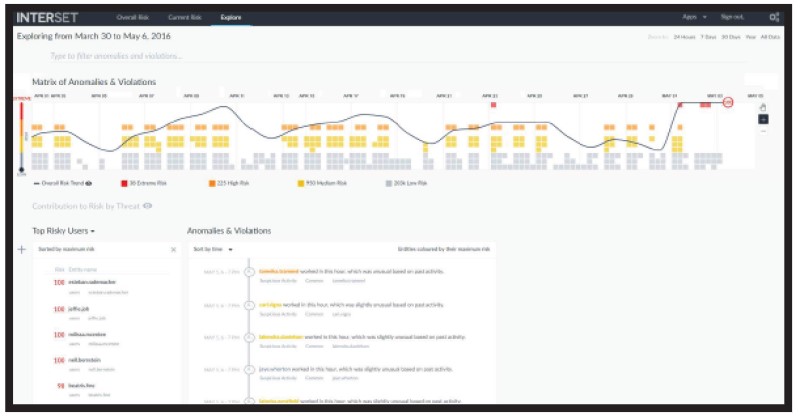
When you click an entity type, the Entities page opens (figure 5), where additional information for the selected entity type is displayed. When you click one of the Top 5 Riskiest Users, the Explore page opens, with the selected user's name applied to the anomalies and violations filter. (Figure 6). Using and administering Interset is covered much more fully in the Interset documentation5.
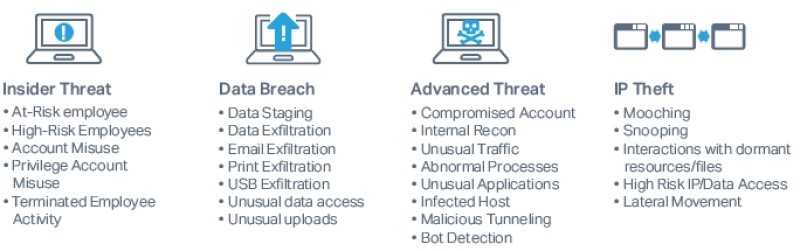
Interset is a powerful addition to the Micro Focus Security Suite and a worthwhile addition to any Security Operations Centre. At a time when there is increasingly a need for effective and comprehensive tools to prevent and detect data breaches, malware attacks and all types of insider threats (as highlighted in figure 2 above) Interset is an excellent option. As one customer working for a $3Bn transportation company writes6 "Interset has exceeded our expectations. It works great and finds those anomalies that we never expected to find. We have conducted a couple of red team tests, and Interset has been able to find everything."
References
1-5 available at microfocus.com
- User and Entity Behavioral Analytics – Flyer.
- What Makes Interset Different Part 1 – Whitepaper
- We Uncover the Threats that Matter – Whitepaper
- Interset UEBA and MITRE ATT&CK – Flyer
- Interset 5.9.2 Documentation
- Gartner Peer Insights https://www.gartner.com/reviews/market/user-and-entity-behavior-analytics/vendor/micro-focus/product/micro-focus-interset-ueba/review/view/1001020