A Corporate Endpoint Data Protection Solution For A Mobile Workforce
In recent years Micro Focus and our customers have experienced an evolution in end user computing, driven by mobility. Organisations are empowering an increasingly mobile workforce, heightening concerns for information security and accountability to increased compliance requirements. Today’s mobile workforces and their requirements for information accessibility is presenting businesses with new challenges when it comes to protecting valuable information that is more widely distributed and accessible than ever before.
Industry research shows that up to half of your organisation’s information resides on endpoint devices. In many cases this distribution of business-critical information is accompanied by the need for the business to maintain visibility, control and accessibility to information that can support needs subject to regulations or that may be responsive to litigation matters. As users and their endpoints become more mobile, the information in their possession is exposed to an increasing number of risks. Historically, hardware failure has been the primary risk to endpoint information.
Mobility makes it more likely that hardware failures occur based upon mishandling of a device. At the extreme, we’ve all heard the stories of someone driving away with their laptop bag left on the roof of the car. In addition to the break-fix related risks to information, businesses now are faced with the aggressive and evolving threat of malware and ransomware that targets their enterprise information, most frequently through the end user.
Today, cyber-criminals are leveraging more than 120 different variants of ransomware to attack all types of businesses. Studies show there has been a 3,500% increase in the criminal use of network infrastructure to run ransomware attacks. These threats are especially grave for highly regulated industries that have strict data privacy and security laws including PCI, PHI, and PII compliance.
With new variants of ransomware evolving every other day and the likelihood of information loss increasing based upon a mobile workforce, businesses must implement a strategy to ensure that the vast amounts of critical information on distributed endpoints is protected and accessible to both end user needs and those of the business. An IDC whitepaper (https://bit.ly/2ShiSO0) - Ransomware Defenses Require Backup and a Comprehensive Security Strategy- states that:
“Investigators are consistently finding a lack of comprehensive defenses that include continuous data protection products that track and save data to disk so that information can be recovered from any point in time, even seconds or minutes ago“.
Micro Focus, as the provider of the Connected portfolio of endpoint backup solutions, has listened to our customers asking for more supporting features from their endpoint backup solution, to extend the value of the solution beyond self-service recovery to support an evolving set of enterprise requirements such as litigation, compliance and information security support.
Connected MX (www.microfocus.com/connectedmx) (CMX) is designed to address the needs of your mobile end users for information protection and accessibility, as well those of your organisation for control and assurance that endpoint information is protected and of maximum value to your business. From its user-based model supporting multiple devices per user to the administrator’s pan-organisation file search, CMX is designed with the following fundamentals to deliver mobile workforce productivity at the edge and business assurance at the core.
Policy based control
The foundation of a business-driven solution is policy. The ability for administrators to define and enforce the rules governing what is, and what is not, backed up and therefore accessible must be capable of being controlled by those designated by the business and not left to the interpretation of the end user, who, depending on the organisation, can number in the hundreds, or the hundreds of thousands.
Connected MX enables the enterprise to define policy to dictate what information should be backed up and thus, accessible to the needs of the end user and the enterprise. Ensuring that the right data is backed up through policy eliminates end user error or omission of information that is critical to the business in support of recovery, compliance, and litigation related requirements.
Policy can be dynamically updated by administrators with organisational granularity to meet compliance requirements. Enterprise control enables a repeatable and defensible process for backup and information preservation from end user devices.
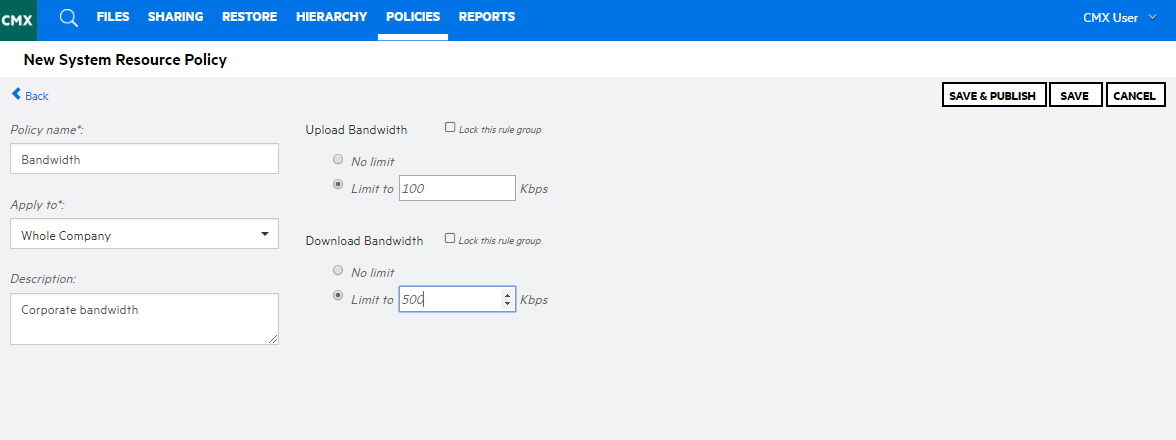
Control via policy is extensive within CMX. In addition to the policies that govern which files should or should not be backed up, flexible policies governing the retention of data, accessibility to data, and the consumption of resources such as network bandwidth are available to allow the customer to tailor the operation of CMX to their specific information protection and retention requirements and to ensure ongoing compliance with those requirements.
Continuous Assured Data Protection
Mobile users are widely distributed with varying and sporadic connectivity over varying types of networks and available bandwidth. Business requirements typically call for the backup of all user data on a user device regardless of type of data or the volume of date in terms of numbers of files or the size of the payload which can exceed half of a terabyte per user.
Connected MX closes gaps in endpoint data protection with its continuous data protection model. Connected MX protects files based upon events (i.e. create, modification) that warrant a backup. Over the course of your day, Connected MX identifies and protects new and changed files, eliminating the need to wait for the next scheduled backup to take place.
Continuous data protection reduces missed daily backups that a single daily backup is susceptible to through an intelligent backup that is “always on” and responsive to backup needs as they arise during the course of your work.
The continuous protection of information also produces more granular restore points enabling users to quickly and easily recover or revert to previous versions of files that they have been working upon.
Simplified, efficient user experience for administrators
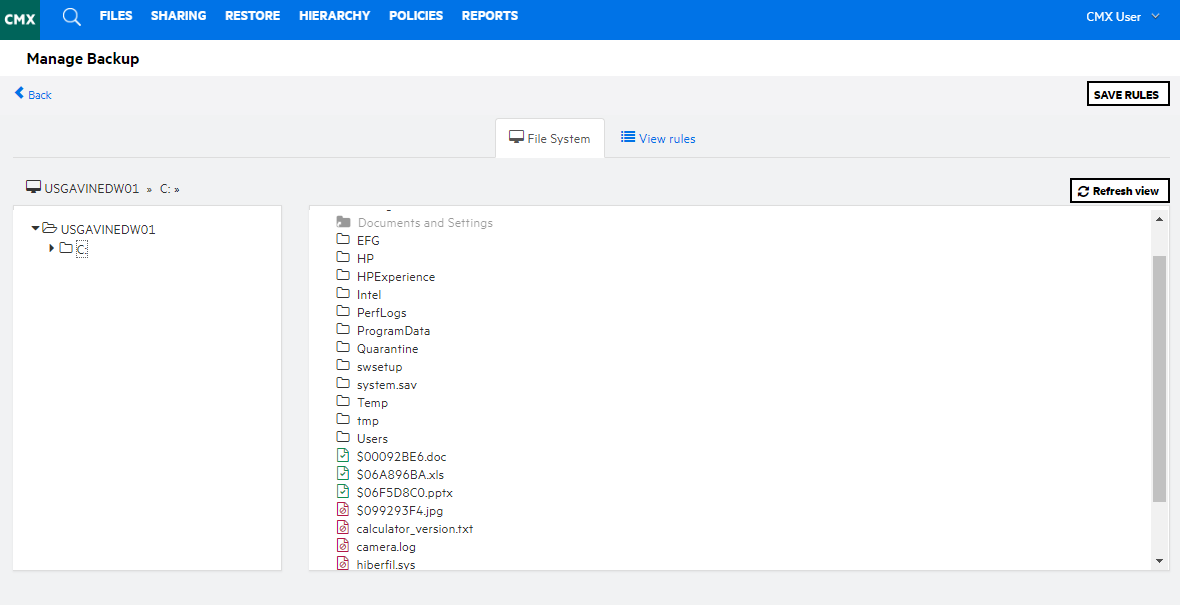
Connected MX’s administrative web interface has been designed to lower costs, simplify, and streamline administrative requirements for large and small deployments. The web console can be accessed from any browser on any device type permitted by policy. Administrators are able to produce an organisational hierarchy to suit their administrative needs. Administrative responsibilities can be securely delegated via roles and limited to specific groups and subgroups of the organisation.
This organisational hierarchy of groups and users can be imported and maintained using the customer directory as the source or created within CMX. From the policy page within the web interface, product behaviour can be defined though policy rules and assigned at either the company or group level.
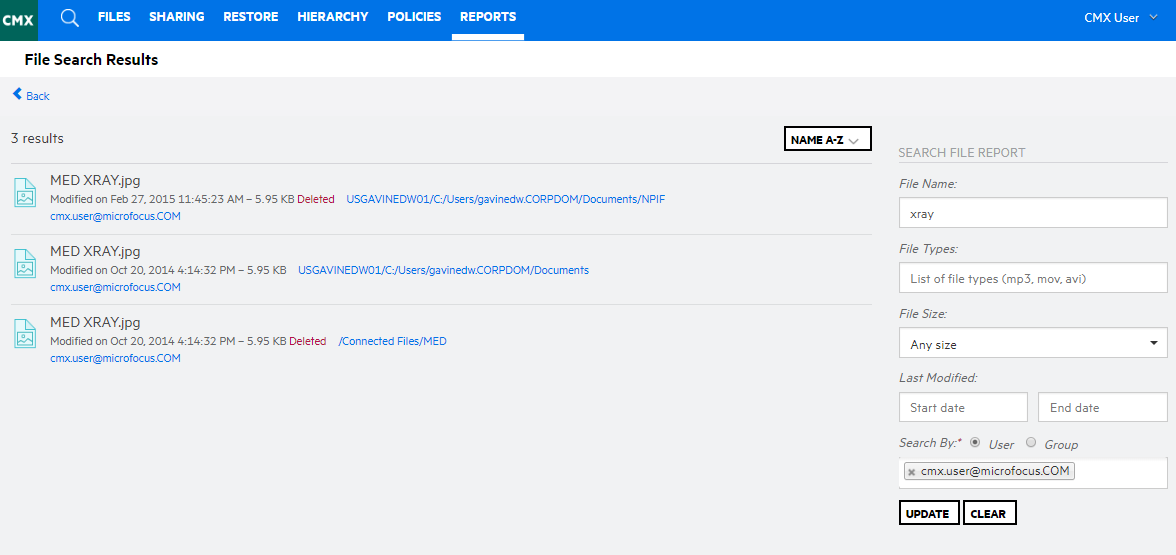
Reporting within the web interface allows administrators to quickly identify instances of concern and gain actionable information for resolution.
Flexible, advanced reporting
It’s critical that the business and more specifically, the administrators of the backup solution be supported by operational analytics enabling KPI based assurance of the solution’s effectiveness.
Connected MX features a rich set of reports that support administrative needs to measure operational effectiveness and insight to the content under protection. These reporting capabilities are powered by an analytics engine that features high performance components such as Micro Focus Vertica.
Reporting within the Connected MX web console includes flexible filter and selection criteria that enables administrators to focus a report on a single user, group, or the entire organisation. Gaining a scalable view of CMX operations is delivered through a series of dashboard graphs that provide a high-level visualisation and click through to root level detail.
Integrating Connected MX report data and metrics with customer reporting standards or systems is easily achieved through the application programming interfaces (API) upon which all reports are based. The APIs allow direct access to CMX reporting information for integration with service desk applications as well as other customer needs.
Enterprise class security
Connected MX features robust security capabilities that are integrated with customer security controls and infrastructure to ensure efficient manageability and compliance. At the foundation of the CMX data security model is a U.S. government certified AES 256-bit encryption.
The Connected MX agent encrypts all data utilising multiple encryption keys to ensure maximum protection of data in motion and at rest.CMX supports options for secure management of encryption keys either by the Connected MX service or by the customer taking control over their keys.
Connected MX easily integrates with customer federated authentication strategies via support of the SAML v2 standard. Through this integration, all aspects of Connected MX authentication are redirected to the customer identity provider where customer security controls are enforced.
Information accessibility
When it comes to an effective endpoint information solution, information accessibility is the key.Connected MX enables intelligent access to information to support the needs of both the end user and the business.
CMX is designed with the analytics capabilities that enable all users and administrators to quickly identify relevant information through search capabilities.
The file preview feature enables file contents to be rendered in place to the user or administrator from web or mobile device apps and eliminates requisite restore of files in order to view the contents. This capability accelerates the use of information to support end user productivity and business decisions.
Upon determination that certain files or entire backup sets need to be retrieved or restored, Connected MX delivers a range of options. From the central console, administrators have the ability to direct a restore to a user’s endpoint. This saves time and money by eliminating the need for administrators to have direct access to the user’s device or involve the user in the restore process.
In support of restores or retrievals that involve multiple users, administrators are provided a purpose-built utility that will restore files to a target file share or device from which the information can be accessed or post-processed to support eDiscovery or archival needs.
In addition to the self-service item level or full restore capabilities of Connected MX, users can download selected files through their browser of choice on any of their devices.
Migration of data from one device to another is also simply achieved with Connected MX. Device refresh as part of a Windows 10 migration is greatly accelerated though the Connected MX data migration capability.
Intuitive, efficient user experience for mobile workers
Connected MX delivers a consumer grade user experience. An intuitive user experience reduces usability issues that result in expensive help desk calls. CMX utilises integrations with Windows Explorer and Mac Finder in order to leverage the native operating system user experience to perform Connected MX specific operations such as managing folder and file selection for backup.
Connected MX is user based and enables a user to assign multiple devices to their user profile. The web interface provides users with a single point of access to all of their data across all devices. The web interface auto adjusts to the size of the device from which it is being accessed ensuring that it is usable from all of the user’s device types.
Policy based access to information from mobile devices is available through native apps for IOS and Android devices.
Bottom line
Business cannot rely on end users to reliably protect the information that is most important to the organisation especially in the face of significant business disruption and financial risks such as ransomware. A solution that is purpose built to enable the protection of, and accessibility to business-critical information is required to meet security, compliance, and regulatory objectives to which the business must fulfil. Connected MX is a robust solution specifically designed to meet the requirements of today’s mobile enterprise.
This article was first published in OHM43, 2019.1, p8-11

