“Data really powers everything we do”.(1) It has been called the “raw material” (2) of business. That is why proper data management is so important. However, the term “data management” is one that is continuously evolving. Today, a variety of factors including the overwhelming growth of data, compliance to data-specific industry and government regulations, and the increasing incidents and sophistication of ransomware are causing organisations to make data management a bigger focus of their activities.
This greater emphasis on data management, along with its continued evolution, is the catalyst for the expanded data management services offered by Micro Focus in a new product released in May – File Dynamics 6.0. At this point, one might logically ask why a brand new product offering is being introduced as version 6.0.
Well, at the core of File Dynamics are the legacy identity-based file system management capabilities of Micro Focus Storage Manager for Active Directory (a product that is still available for purchase). File Dynamics was engineered from this legacy system, but then greatly expanded the policy-based management capabilities from merely Identity-Driven policies, to now Target-Driven policies.
Product Overview
File Dynamics provides extensive services to address the expanding requirements of network data management. Identity-Driven policies automate tasks that are traditionally done manually, resulting in cost savings and assurance that tasks are being performed properly. Target-driven policies offer data migration, remediation, cleanup, and protection from data corruption and downtime through nearline storage backup of vital data, referred to as “High-Value Targets,” enabling quick recovery of files and their associated permissions.
Data Management Delegated to Data Owners
An important aspect of File Dynamics is the introduction of “Data Owners” and their role in performing limited, but important data management tasks. A Data Owner is a user specified in a File Dynamics Target-Driven policy who is enabled to perform data recovery and remediation tasks, based on the user’s designation as a Data Owner, and the user’s familiarity with the data.
For example, compared to a regular IT staff member, an employee in the Legal Department of an organization is much more knowledgeable about the files and folders being stored and accessed by the Legal Department employees. Therefore, it makes sense for an administrator to designate a user in the Legal Department to be a Data Owner for that department.
Data Owners are enabled to recover data and remediate the location of sensitive files to more secure locations.
Identity-Driven Policies
Identity-Driven policies affect user and group objects that make up the Microsoft network operating system’s directory service – Active Directory. A User Home Folder policy or a Group Collaborative policy specify the settings for managing network storage areas for user and group objects respectively in Active Directory. For example, you could create a User Home Folder policy that was associated with the Human Resources organisational unit of your Active Directory forest. The settings within that policy would then apply to all user objects that reside in that organisational unit.
The settings within an Identity-Driven policy specify how user and group data is automatically provisioned, how common management tasks are automatically conducted, and how it is automatically cleaned up.
We covered the Identity-Driven features in a previous article on Storage Manager (OHM35, 2016/4, p26-28), so the focus here will be on the new Target-Driven policies.
Target-Driven Policies
Through Target-Driven policies, File Dynamics performs management tasks through policies associated directly with a network share of a folder. Target-Driven policies include Data Location policies, Content Control policies, Workload policies, and Epoch Data Protection policies.
Data Location Policies policies are the means of copying folders and their contents to a target parent folder. There is an option to remove the files from the source location after they have been copied. For example, if you were performing a server consolidation or moving data from a server to a NAS device (or vice versa), you could do so easily using Data Location policies.
Content Control Policies. Similar to Identity-Driven file grooming, Content Control policies remove files according to file type, age, size, when last accessed, and more. From any file path, you can either vault files to a new location or delete the files altogether. You could use this feature for example, to easily delete temporary files and in the process, make much more disk space available on your storage devices.
Workload Policies in File Dynamics provide the ability to handle work processes initiated from other applications. For example, reports generated in Micro Focus File Reporter that specify the locations of files containing credit card or U.S. Social Security numbers (a new capability introduced in File Reporter 3.5) can be imported into the Data Owner Client where a designated Data Owner can remediate the location of these sensitive files from an open share, to a more secure location. This approach empowers organisations to provide automated network file system security remediation approved by a gatekeeper familiar with the files.
Epoch Data Protection Policies.
As organisations have had to deal with the increasingly devastating effects of ransomware, they are looking to solutions that provide data continuity. Data continuity is a term that includes the measures taken to safeguard the integrity and availability of critical data so that when an event takes place that either corrupts the data or disables access to it, restorative remediation can take place quickly and with minimal disruption.
Logically, one might conclude that the organisation’s backup system would take care of this, but the sophistication of recent ransomware attacks has many security experts recommending that you keep multiple backups3 in various locations, with restrictive administrative and system access.4
Moreover, restoring data from traditional backup systems can be time consuming as it oftentimes requires IT administrators to sort through the contents of an entire system backup.
In addition to safeguarding against ransomware attacks, there are other reasons why an organisation would want to protect data through additional data continuity measures. These include:
- Protecting data from inadvertent corruption, loss, or deletion
- Restoring the data back to how it existed at a particular point in time in the past
Similarly, organisations might need to protect and recover the permissions of High-Value Targets, including:
- Lost or destroyed permissions
- Inadvertently changed permissions
- Permissions as they previously existed at a particular point in time in the past
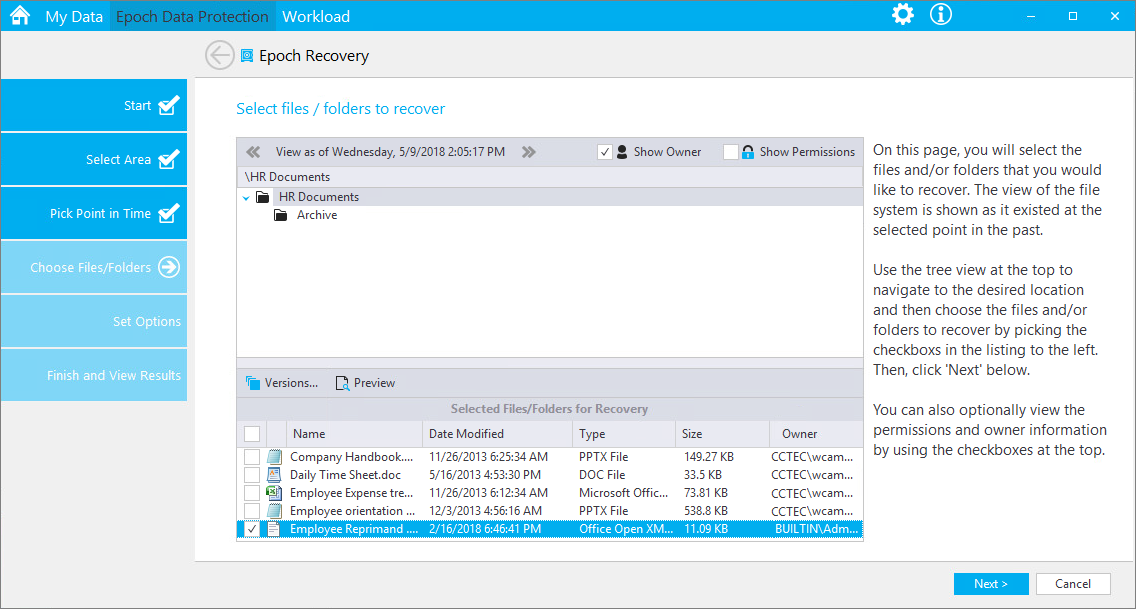
Epoch Data Protection policies allow customers to maintain nearline standby views of High-Value Target folders stored in the network file system. Data Owners can view and access the archive of the High-Value Target as it existed at a selected point in the past. In essence, it is a “time machine” for the data and associated permissions on the High-Value targets.
Archived files are located in a “Collection” of “Epochs.” An Epoch consists of the directory structure and associated metadata at a point in time. The Collection is stored in a nearline repository called a “File Store.” Epochs are saved to the File Store through a proxy with no direct user access to the Collection. This creates a confined repository on the network that cannot be compromised by a user.
Recovering a file from the File Store is a multi-step process. Using the Data Owner client, the Data Owner first opens an Epoch and can then see the contents of the Epoch, with even the option of opening a “View” of an individual file.
The View is not the actual file, but a complete rendering of the file. Upon determining which files to recover, the Data Owner then makes a recovery request for those files.
The Data Owner Client authenticates to the Engine and the Engine then delegates the recovery to the Phoenix Agent, which recovers the files to either the location where the file existed previously or to a location of the Data Owner’s choosing.
Unique Benefits
When it comes to data continuity, the Epoch Data Protection (EPD) offered in File Dynamics offers many enhancements in addition to vital backup systems.
- The EPD interface is easy to use and administer. Using either a wizard or a console, you can locate a file you want to recover. Locating and selecting files is similar to locating files in the Windows Explorer interface. Administrators who have had to work with the complex user interfaces of other backup systems will find the EPD interface very intuitive.
- With File Dynamics you can designate specific Data Owners to be in charge of restoring data and permissions from High-Value Targets. This offloads the responsibility from the overworked IT staff and in the process, enables a faster response and restoration time from the Data Owner—a critical factory in effective data continuity.
- EPD uses limited read/write access to backup locations—a remedy for diminishing the threat of ransomware. With restricted network access to the protected High-Value Targets, data and their permissions remains protected from ransomware and other malware threats.
- EPD lets you back up High-Value Targets as frequently as you would like and permits the Data Owners to verify the integrity of the backups. According to the Software Engineering Institute at Carnegie Mellon University, “The single most effective deterrent to ransomware is to regularly back up and then verify your system.” 5
- The EPD repository is one more repository for your critical data. Security analysts recommend a multi-tier approach to provide more reliability with backups.6
- EPD policies archive files quickly. That is because only files that have been modified since the last saved Epoch are backed up. However, when you open the new (or any) Epoch, it will contain all of the archived files in the High-Value Target – not just the modified files.
- As you locate a file for recovery, you can view a complete rendering of the file to verify that the selected file is indeed the file you want to recover.
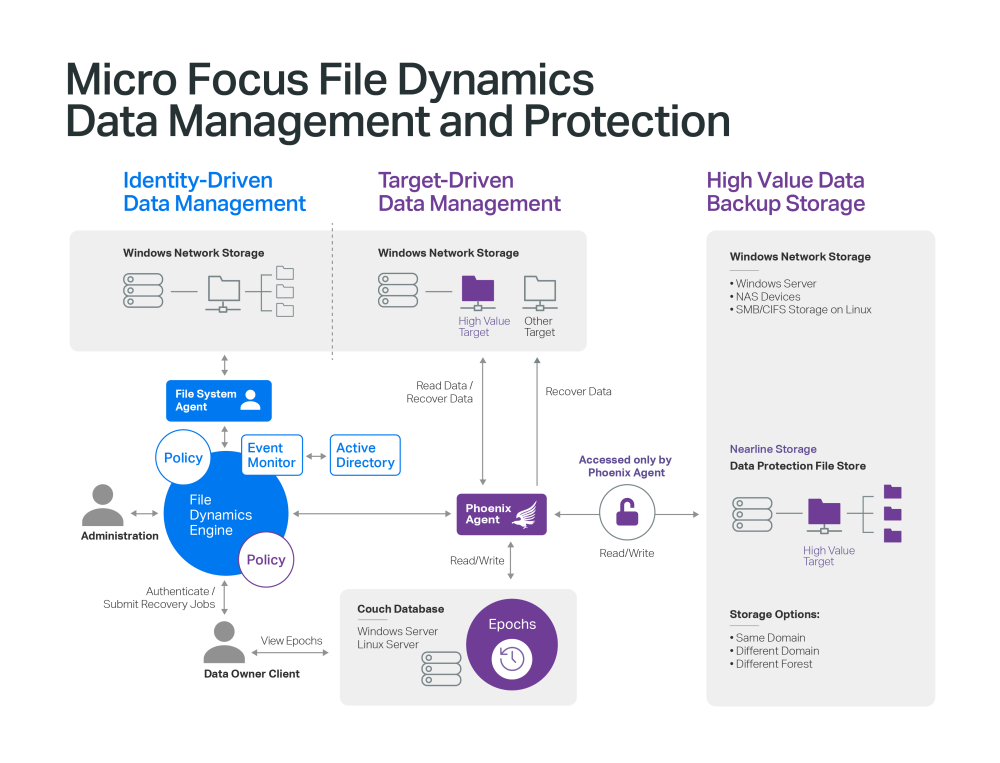
Expanding Data Management Services
Data management requirements have changed dramatically since we introduced our first data management product—File System Factory in 2003. Back then, the principle focus of the product was completing the account automation chain of identity management systems by automating the provisioning of network user storage locations in synchronization with the automated account provisioning provided by the identity management system. The product became an instant success—especially within organisations with a large number of user accounts.
Over time, the product name was changed to Storage Manager as capabilities were expanded to include features to solve other data management challenges—challenges that included addressing data growth, security, compliance requirements, data loss prevention, and more. As data management continues to evolve and its requirements continue to expand, Micro Focus is committed to continue to address those challenges.
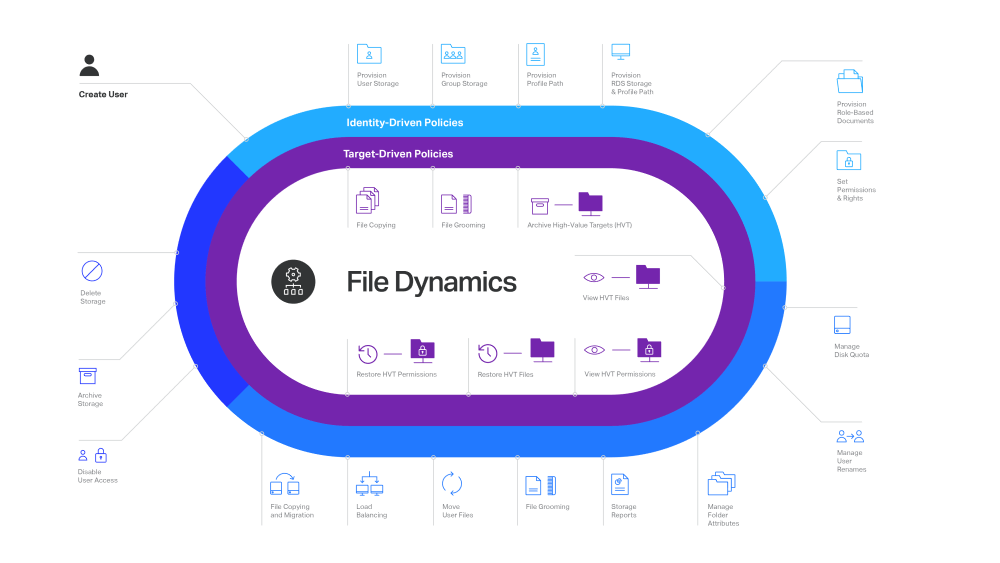
With Identity-Driven policies providing automated user and collaborative data management, combined with Target-Driven policies that provide selected storage management and data protection, you have a data management system in File Dynamics that meets an extensive set of today’s data management challenges.
As data management requirements continue to evolve, so will File Dynamics. Development plans are now in place for even more Target-Driven management capabilities that will be introduced in future releases.
Conclusion
Identity- and Target-Driven policies in File Dynamics together work to manage an extensive set of data management tasks that will save you money, help meet your compliance objectives, provide assurance that management tasks are being performed correctly, and provide you confidence that files located on High-Value Targets are being backed up and can be recovered quickly.
As network-stored data continues to grow, as regulations for data storage access and privacy continue to become more stringent and complex, and as threats from malware continue to wreak more and more devastation, the data management capabilities of File Dynamics are needed more than ever.
References
- Jeff Weiner, CEO, LinkedIn
- Craig Mundie, Senior Advisor to the CEO, Microsoft
- Will your backups protect you against ransomeware?, Maria Korolov, CSO Online, May 31, 2016
- Ransomware Damage Report: 2017 Edition, Herjavec Group, May 24, 2017
- Ransomware: Best Practices for Prevention and Response, Alexander Volynkin, Jose Morales, Angela Horneman, May 31, 2017
- Will your backups protect you against ransomeware?, Maria Korolov, CSO Online, May 31, 2016
This article was first published in OHM Issue 41, 2018/2, p27-30