Over the past 20 years, ZENworks has continuously evolved to help IT personnel manage the lifecycle of their endpoint devices, growing from its inception as a client management tool for Windows devices to its current state as a Unified Endpoint Management (UEM) solution for traditional Windows, Linux, and Mac devices as well as iOS and Android mobile devices.
Today, ZENworks continues to execute on its primary goals:
- Enable administrators to effectively manage a variety of platforms
- Provide efficient resource and application deployment
- Empower users through self-service
- Secure data and devices
- Simplify management via consistent workflow paradigms in a single management console
So, what’s next in the continuing evolution of ZENworks? We will, of course, continue to enhance the current ZENworks UEM experience through increased capabilities around mobile device management, self-service, and traditional device support.
In addition to staying the course in those areas, we are increasing our focus on the security-related capabilities, moving ZENworks from a Unified Endpoint Management solution to a Secure Unified Endpoint Management solution.
Why Secure Unified Endpoint Management?
To understand the increased focus on Secure Endpoint Unified Management, you only need to look at the trending threats to endpoints today:
- Rising Malware Attacks: While malware attacks have existed for many years, they have increased in both frequency and creativity over the past several years. What started as viruses and worms has evolved into more sophisticated attacks such as ransomware and cryptocurrency mining (the ever-increasing and damaging CoinMiner programs that steal others’ computing resources).
- Increasing Software Patches: In 2017 alone, operating system vendors Microsoft, SUSE, Red Hat, and Apple combined to release over 6000 patches. Add in major software vendors Mozilla, Adobe, Google, and Oracle and that number grows to over 6500.
- Growing Number of Operating Systems and Applications: IT departments are challenged with continuing to support existing platforms such as Windows, Linux, and Mac while ramping up support for mobile platforms such as iOS and Android. This effort, and the corresponding security concerns, are only amplified by the number of operating systems and applications available for each platform.
- On-the-Move Users with Sensitive Data: The number of mobile users continues to increase. For many, the days of static workspaces have been replaced by roaming laptops and mobile devices. These on-the-move devices carry sensitive data that needs to be secure. The 2016 Kensington IT Security & Laptop Theft report showed that one laptop is stolen every 53 seconds, over 70 million smartphones are lost every year, and 4.3 percent of company-issued smartphones are lost or stolen every year.
- Shrinking IT Resources: At a time when security threats and concerns are reaching an all-time high, IT organizations are being asked to do more with reduced staffs and budgets.
- IT administrators need all the help they can get to battle these ever-increasing threats. And with its current security capabilities, planned security enhancements, and potential integration opportunities with other Micro Focus security products, ZENworks provides a solid security solution that continues to grow stronger with each release.
ZENworks Security Today
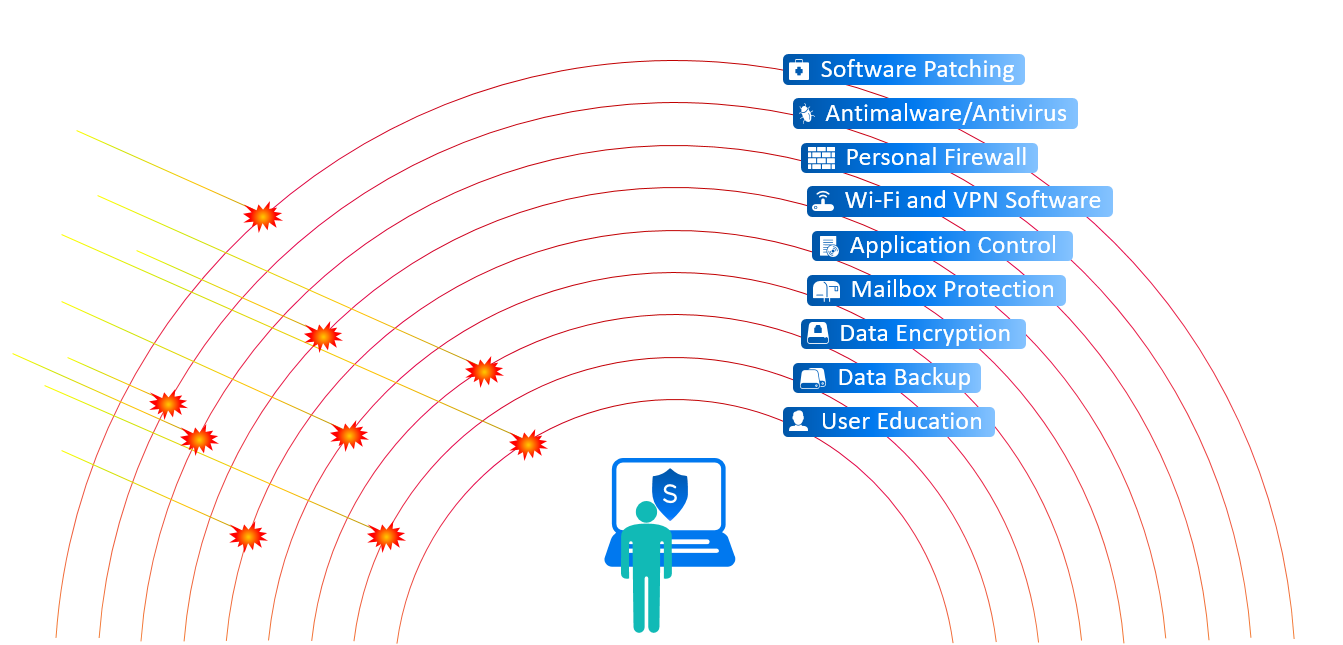
Endpoints present a broad attack surface. Securing devices against threats requires multiple layers of protection (figure 1).
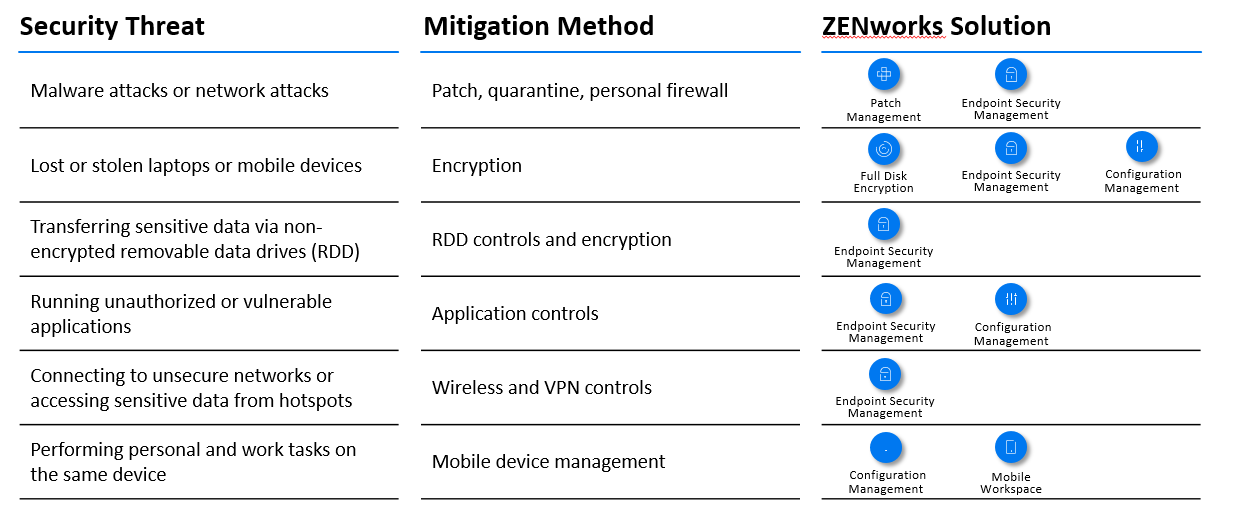
Today, ZENworks mitigates many of these security threats through solutions provided by ZENworks Patch Management, ZENworks Endpoint Security Management, ZENworks Full Disk Encryption, and ZENworks Configuration Management, as shown in the following table.
ZENworks Security Tomorrow
Moving forward, we’ll continue to add to the ZENworks security capabilities. In the next release (ZENworks 17 Update 4), planned enhancements to ZENworks Endpoint Security Management include folder encryption, filename wild card support for application control, and access control for Windows Portable Device storage.
Security enhancements in ZENworks Configuration Management include added configuration of Android device control settings.
But the transformation of ZENworks from a UEM solution to a Secure UEM solution involves much more than simply adding additional security functionality to endpoints.
It also involves helping you see the security status and risk level of devices in ZENworks as well as in other security solutions your organisation might be using. It involves being able to monitor and remediate emerging threats through known security methods such as the Common Vulnerabilities and Exposures (CVE) standard.
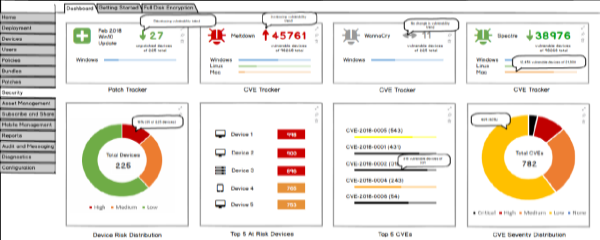
This enhanced security approach debuts in the ZENworks Atlantic and ZENworks Atlantic Update 1 releases that are tentatively scheduled for 2019. The ZENworks Atlantic release will introduce detection and remediation of vulnerabilities based on the Common Vulnerabilities and Exposures (CVE) standard.
Using a new Security dashboard, you’ll be able to track an individual CVE and monitor the remediation status of impacted devices. You’ll also be able to monitor groups of CVEs based on criteria such as the number of impacted devices or the CVE severity rating.
Of course, you will be able to act on the dashboard data to apply all patches (in one deployment) needed to remediate the vulnerability. The low-fidelity mockup shown below gives an idea of what this dashboard will look like.
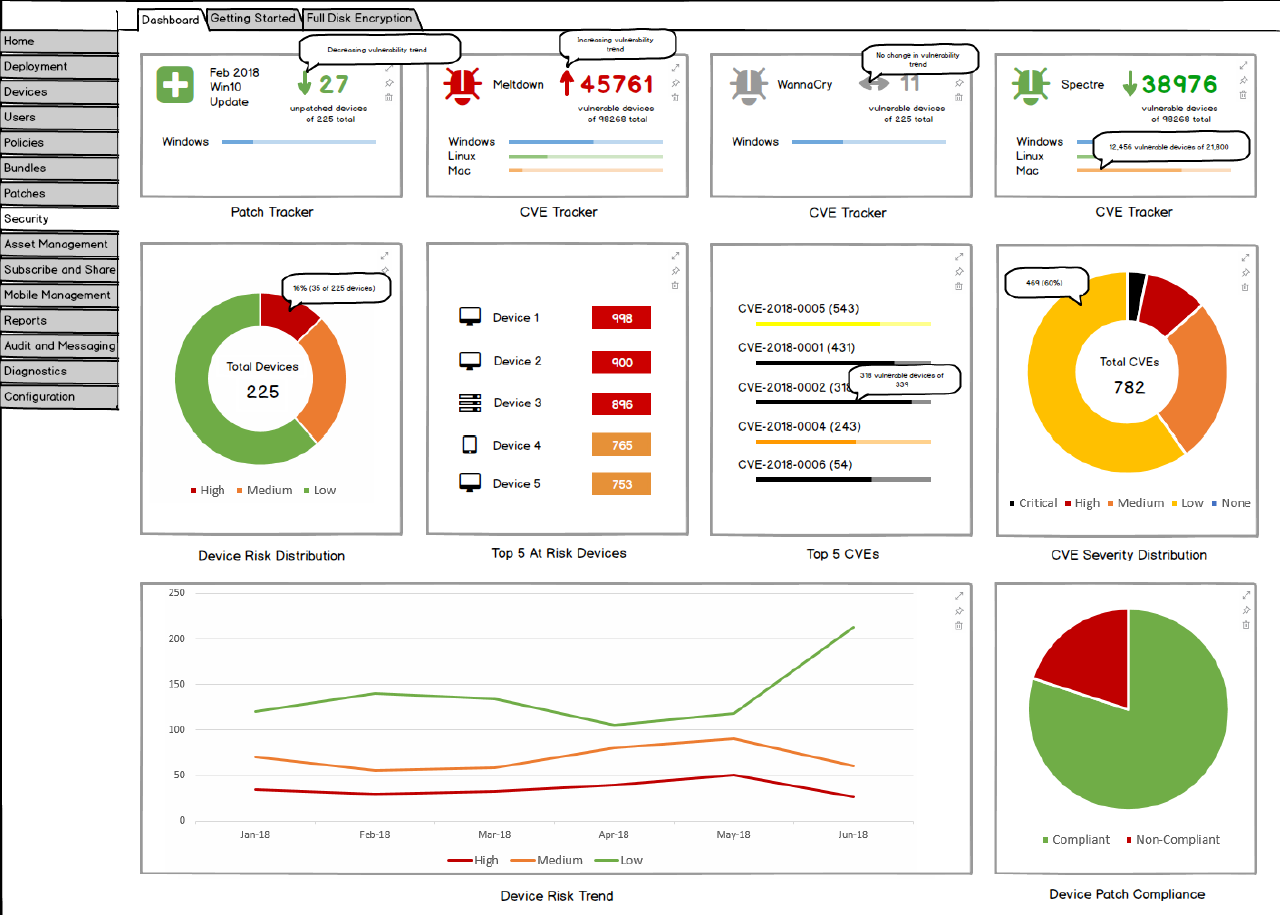
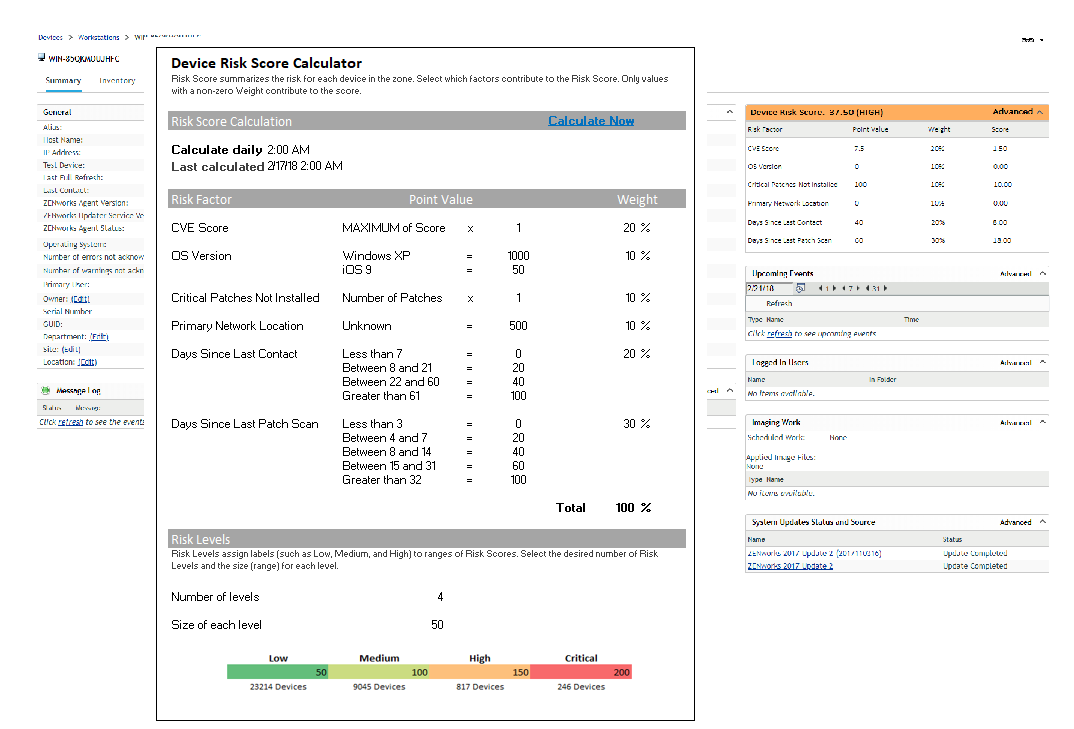
The ZENworks Atlantic Update 1 release will introduce the concept of Device Risk, allowing you to identify the at-risk devices in your organisation. You will be able to define the risk factors used to calculate a risk score and risk category for each device.
This could be factors such as the CVEs applicable to the device, the location of the device, the encryption status of the device, or the last contact time with the zone. With high-risk devices identified, you could then take actions to lower the risk as necessary.
(figure 4).
Future security additions are not limited to in-product enhancements only. ZENworks gathers tremendous amounts of endpoint data that, when shared with other security products, can allow for increased awareness of risks within an organisation.
ZENworks 2017 Update 3 added the ability to output audit and system events in CEF format to Syslog servers. These events can be correlated in Security Information and Event Management (SIEM) tools, such as ArcSight and Sentinel, to alert administrators when specific events occur on the system.
Moving forward, we’ll look at continued integration opportunities with other Micro Focus security products in order to provide customers with the most secure environments possible.
Final Thoughts
Endpoint security has never been more needed than it is today. Security breaches can lead to loss of customer confidence, cost both time and money, and lead to regulatory sanctions. Through its solid foundation of security policies and patching, ZENworks provides multiple layers of protection to mitigate risks and secure endpoints.
Extending on this foundation is the focus of our upcoming releases. Soon, you’ll soon be able to better expose the vulnerabilities impacting your endpoints, evaluate the risks associated with these vulnerabilities, share that risk data with other security solutions, and take action to mitigate those risks.
Unified Endpoint Management to Secure Unified Endpoint Management – the next step in the ongoing evolution of ZENworks.
Disclaimer: This article includes information about forward looking capabilities. While we strive to ensure that we deliver the functionality described in the approximate timeframe, market priorities can shift, customer issues can occur, and other factors not within our direct control can cause priorities to shift. The information presented represents the best possible information we have at this time and should be seen as a directional indicator.
This article was first published in OHM Issue 42, 2018/3, p5-7.