IT Security has grown over the last few years to become a real business issue engaging all business functions. Security isn´t just a problem for the IT department anymore, trying to arrange downtime for a server to implement some patches. New threats have risen such as: ransomware (the recent Wannacry episode for example); botnets running on IOT Devices (e.g. the Mira Botnet) attacking critical infrastructure components of the internet (experts(1) say the DDoS attack that caused widespread disruption was the largest of its kind in history); or targeting a specific company’s main business model (e.g. hacker holds Netflix to ransom over new episodes of Orange Is The New Black(1).
The steps that should be taken to minimise the effects of these attacks on your infrastructure and data are various and depend on the different types of business risks and the IT services running. However thorough planning and consultations are key points at all stages.
Before all of those necessary steps on defining processes, implementing hardware (e.g. two factor authentication) or software (e.g. Intrusion detection systems), there are many basic actions to be taken that are often forgotten or not fully considered. Most of the basics rely on tools already installed or software available in the OS distribution along with some simple configurations changes. Some of these basic steps enhance the security of a system by not interfering with the service running on top. These are low hanging fruit. This article will highlight just two techniques that operating teams should consider essential.
Intrusion Detection
One easy to implement step is to run a simple host based Intrusion Detection system such as AIDE (2) (Advanced Intrusion Detection Environment). AIDE is a free and open source tool for Linux systems that has been developed over a number of years. AIDE is not installed by default on SUSE Linux Enterprise Server but to install it, either use Computer > Install Software, or enter zypper install aide on the command line when logged in as root. AIDE cannot protect a system by preventing an attack, but can help to stop it from running.
Studies show that the access points used by attackers are often held open by them through backdoors over a long period of time. AIDE helps to identify and report those backdoors on the system. The procedure for implementing AIDE is as follows.
The first step has to be taken before any “contamination” by third parties could have taken place. This should be directly after the installation phase of the operating system.
AIDE is a command line tool and on first running it scans the server and creates a database file based on a number of different file attributes.
This database reflects the golden image/status of the server. The database file should be saved to a different location. Subsequently when the server is in active use AIDE can then be run again and the new scan compared against the database to check the integrity of all files as shown in figure 2.
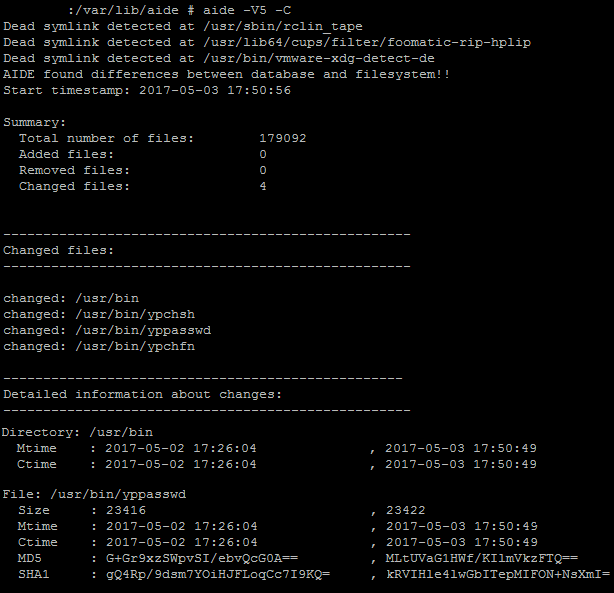
A backdoor is shown, which an attacker installed on the system by replacing a file which is infrequently patched and is often out of focus of the system administrator. This file is just an example of files that are not usually in the daily security focus. In this case the simple scheduled usage of the all known rpm commands would have also shown this “backdoor”. Infrequently used parameters such as rpm –verify would show that the file has changed as it´s a file known to the rpm database, (because it´s part of an installed rpm and not a tar file). That is one of the many benefits of software packaged as rpms.
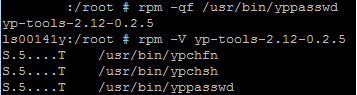
AIDE has the advantage that it shows changes in the directory itself; or will show if files have been added to the directory. It´s always good to double check the well known phrase “No one has changed anything”.
AIDE should be run regularly, ideally as a cron job, so that you have an insight of changes on the server. It has a large number of parameters by which you can search the database. Table 1 highlights the most common search parameters.
It’s one thing to check your system for integrity and report on it, but another thing to prevent attacks or at least keep the hurdles high and make attacks as hard as possible. This is often known as hardening the operating system and, as we also know, often not used enough. In the next little scenario I would like to show the necessity of certain basic steps. The exploits used could have been prevented by following basic security steps on hardening the server.
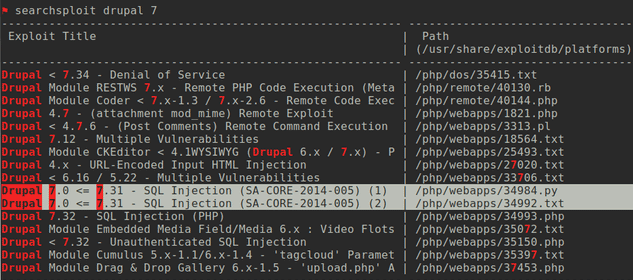
The server in mind runs an outdated version of Drupal - a web content management system (CMS). By using different tools such as nmap, nikto or even telnet it´s very easy to get information on the running version of the cms just by using the open port 80 and asking nicely (as figure 4 shows).
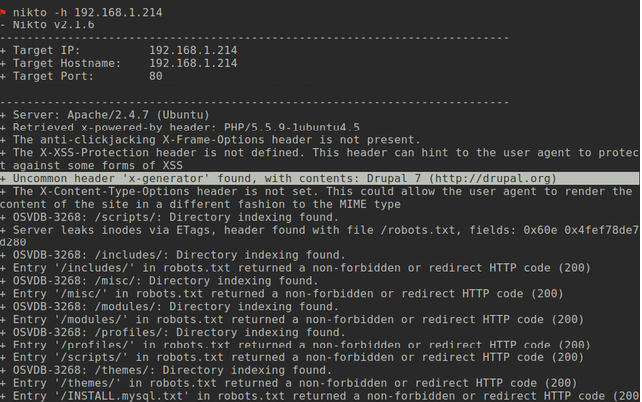
The technique is called banner grabbing (3) and if not properly deactivated4 reveals much useful information. Footprinting and reconnaissance are one of the first steps an attacker undertakes to search for the weakest link and a way into your system. By searching the version of the running OS or application the attacker can use available databases (5) to search for vulnerabilities, and frequently get instantly the necessary code for SQL injections or privilege escalations. The easy way is to search the database via the command line (figure 5).
Attackers frequently gain access in the first place as an unprivileged user or through a technical account such as wwwrun or tomcat. The next step is to get some privilege escalation working. Attackers often make use of misconfigured services. For example, granting rights via sudo to scripts or applications with shell escape sequences.
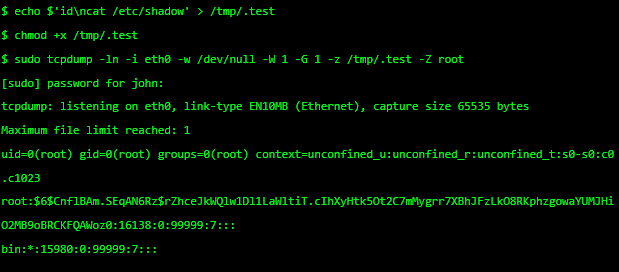
Basic steps such as filesystem security are often not given sufficient thought, although it is in many cases one of the first barriers for an attacker to overcome, and it should be made as difficult as possible. An example is the /tmp directory which is often underestimated in its relevance for system security. All users can write to the /tmp directory, and if not held in a separate partition this can benefit the attacker.
The attacker can hard-link files with SUID settings to /tmp, which is not so bad as users already have access to the SUID file itself. But as soon as the original file is updated, the hard-link breaks and the attacker then has his own version of the SUID file which can then be used and expanded in functionality while still having the benefit of the SUID feature. Simple steps like a separate partition or/and the mount option noexec in /etc/fstab will prevent any execution of bad binaries.
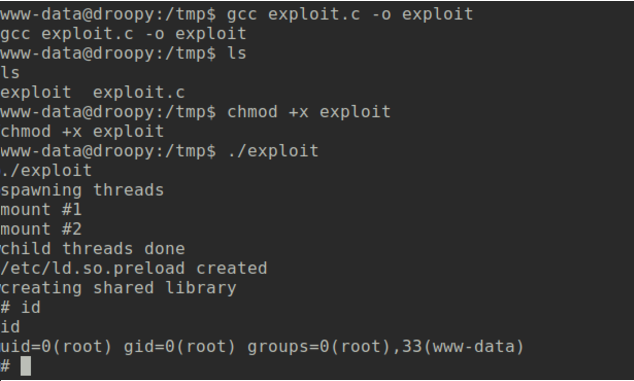
As time is important, attackers often take advantage of pre-installed software, which plays into their hands. In many cases a c compiler, like the gcc, is installed on a server as it was needed for a software installation process6. An installed c compiler makes it easy for the attacker to write and compile code and build a privilege escalation binary (7) without bringing malicious software into the company by penetrating the firewall.
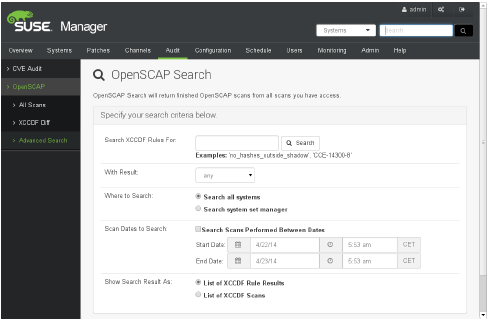
SUSE has its own manual called the Server Tuning and Hardening Guide which is a great resource to start with. Two other guides or frameworks are the CIS benchmarks (8) and the openSCAP (9) framework with its different Guidelines. The CIS benchmarks are a set of configurations packaged together with explanation and the commands or scripts needed to check the settings, which makes it easy to implement in every different configuration framework. The openSCAP framework features the de facto standards for secure system implementation based on varying demands and is implemented within SUSE Manager for easy review of system settings (figure 8).
Simple Steps
All these different steps together help to secure the operating system and are a huge step towards a more secure server. Bugs in software will still exist in the form of zero day exploits and unpatched systems but simple steps such as basic hardening and reporting can make the difference between blindness and sounding the alarm for attention during an attack.
References
- www.cyberdefensemagazine.com/the-gcc-cyber-security-market-is-booming/
- https://en.wikipedia.org/wiki/Advanced_Intrusion_Detection_Environment
- https://en.wikipedia.org/wiki/Banner_grabbing
- www.owasp.org/index.php/Securing_tomcat and www.ibm.com/developerworks/library/se-banner
- www.exploit-db.com
- Prerequisites : VMware or Oracle Database
- www.exploit-db.com/exploits/40847/
- www.cisecurity.org/cis-benchmarks/
- www.open-scap.org/
- www.suse.com/documentation/sles11/book_security/data/sec_aide_setup.html
This article was first published in OHM Issue 37 (2017/2), p29-31.
]


