We live in a time of constant technological change. What is new today has the potential to be obsolete a month from now. In many organisations, users are racing to embrace new technology. They are finding new ways to work, collaborate, and communicate. They are blurring the boundary between different devices, expecting to switch seamlessly from one device to another without losing data or productivity. They are becoming less hesitant to resolve problems themselves. While with the advent of application stores, they expect everything to be downloadable, in an instant, from a store.
 In this new world, many IT organisations are falling behind, reacting to these changes rather than anticipating them. Others are increasingly realising that their current set of tools are not sufficient to deal with this pace of change. The diversity of devices—desktops, laptops, smartphones, tablets, and even Internet of Things (IoT) devices—is a huge challenge by itself. When these devices are personally owned by employees, they can present the added challenge of determining the extent to which they can be managed.
In this new world, many IT organisations are falling behind, reacting to these changes rather than anticipating them. Others are increasingly realising that their current set of tools are not sufficient to deal with this pace of change. The diversity of devices—desktops, laptops, smartphones, tablets, and even Internet of Things (IoT) devices—is a huge challenge by itself. When these devices are personally owned by employees, they can present the added challenge of determining the extent to which they can be managed.
Additionally, depending upon device capabilities, different tools may be needed to manage them, but these tools can differ in the degree of management control offered. However, even with such diversity of tools and devices, an IT administrator is always expected to ensure that:
- Data on devices is secure.
- Devices themselves are secure from external and internal threats.
- Devices are compliant with security and organisational policies.
- Devices have the correct set of tools and applications to enable employees to work in an easy and efficient manner.
Given the diversity of devices and business needs versus the requirement for security and enablement, one of the ways an IT organisation can manage things effectively is by deploying a Unified Endpoint Management (UEM) solution.
What is a UEM solution?
Historically, the endpoint management market has been neatly divided between PC Life Cycle Management and Enterprise Mobility Management (EMM)/Mobile Application Management (MAM). Different solutions existed for each category and there was almost no overlap. Fast forward to today and you find many vendors offering a suite of products through which both PC and mobile devices can be managed. So is this what it means to be a UEM solution?
While researching for this article, I found quite a few thoughts on what a UEM solution is. Some think it is a suite of solutions that can manage all devices in an organisation. Some say that it is one solution that allows all types of devices to be managed. Still others stress that it is the ability to manage everything in a similar manner.
While each definition has merit, the one that I find most appealing combines points taken from all three: One solution to manage all devices in a similar manner.
- One Solution - A single solution reduces the strain on training, resources (both hardware and personnel), and processes required to support multiple solutions.
- Manage All Devices - A single solution isn’t very effective if it doesn’t allow you to manage all devices in your organisation. The end result is multiple solutions that increase management overhead.
- Similar Manner - I find that managing devices in a similar manner is the most useful characteristic of a UEM solution. Given the diverse set of devices present in today’s organisation, what matters most is that the same set of principles and processes can be used to manage this varied set of devices. This ensures that an introduction of new device types doesn’t result in a completely new set of processes. Most importantly, this standardisation plays a key role in lowering the overall costs of deployment and maintenance, which is so important in today’s world of shrinking IT budgets.
Are all UEM solutions equal?
No. As in any other solution space, even in the endpoint management space, not all UEM solutions are equal. Currently there are two types of UEM solutions:
- Traditional PC lifecycle management solutions that are gaining Enterprise Mobility Management (EMM) and/or Mobile Application Management (MAM) capabilities
- Traditional EMM solutions that are adding PC lifecycle management capabilities
For the most part, capabilities for managing the traditional PC lifecycle in EMM solutions (the second solution mentioned above) are limited in nature, although in the future these may evolve as OS vendors continue to enhance the native manageability of PC devices. As a result, if an organisation currently has a large PC base, it may make the most sense to deploy a solution that offers a rich set of PC lifecycle management features coupled with EMM capabilities (the first solution mentioned above).
ZENworks 2017 – a UEM solution
ZENworks has always boasted a strong feature set in the PC Lifecycle Management market. The upcoming ZENworks 2017 release introduces EMM capabilities into ZENworks Configuration Management (ZCM), allowing you to manage PC and mobile devices all in a single solution.
Relying on the single management console—ZENworks Control Center (ZCC)—and a set of common work flows, IT administrators can easily manage mobile devices just like they would a non-mobile device. Most importantly, ZENworks 2017 makes it possible to manage all of an organisation’s devices in a similar manner, firmly establishing itself as a true UEM solution.
So, let’s take a quick look at the key capabilities being introduced with ZENworks 2017 and how they ensure that IT administrators finally have a world class UEM solution to work with.
Managing mobile devices just like any other device
ZENworks 2017 expands its core feature set to enable management of iOS, Android, and Windows devices (in EAS mode). However, in what may seem counter-intuitive to the mobile push, ZENworks 2017 doesn’t really scream mobile. So the question arises—why so? The answer—because a lot of effort has gone into ensuring that a mobile device is treated just as another device to be managed.
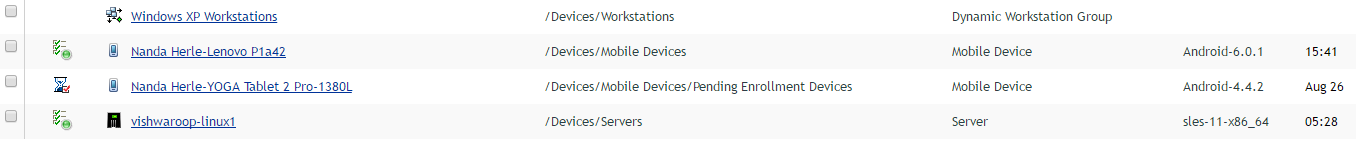
This approach provides the flexibility to extend features available for non-mobile devices to mobile devices in a seamless manner. More importantly, this approach ensures that an IT administrator can manage all devices in a similar manner without worrying about the underlying nature of the device. Mobile specific details, wherever required, are surfaced in an unobtrusive but effective way.
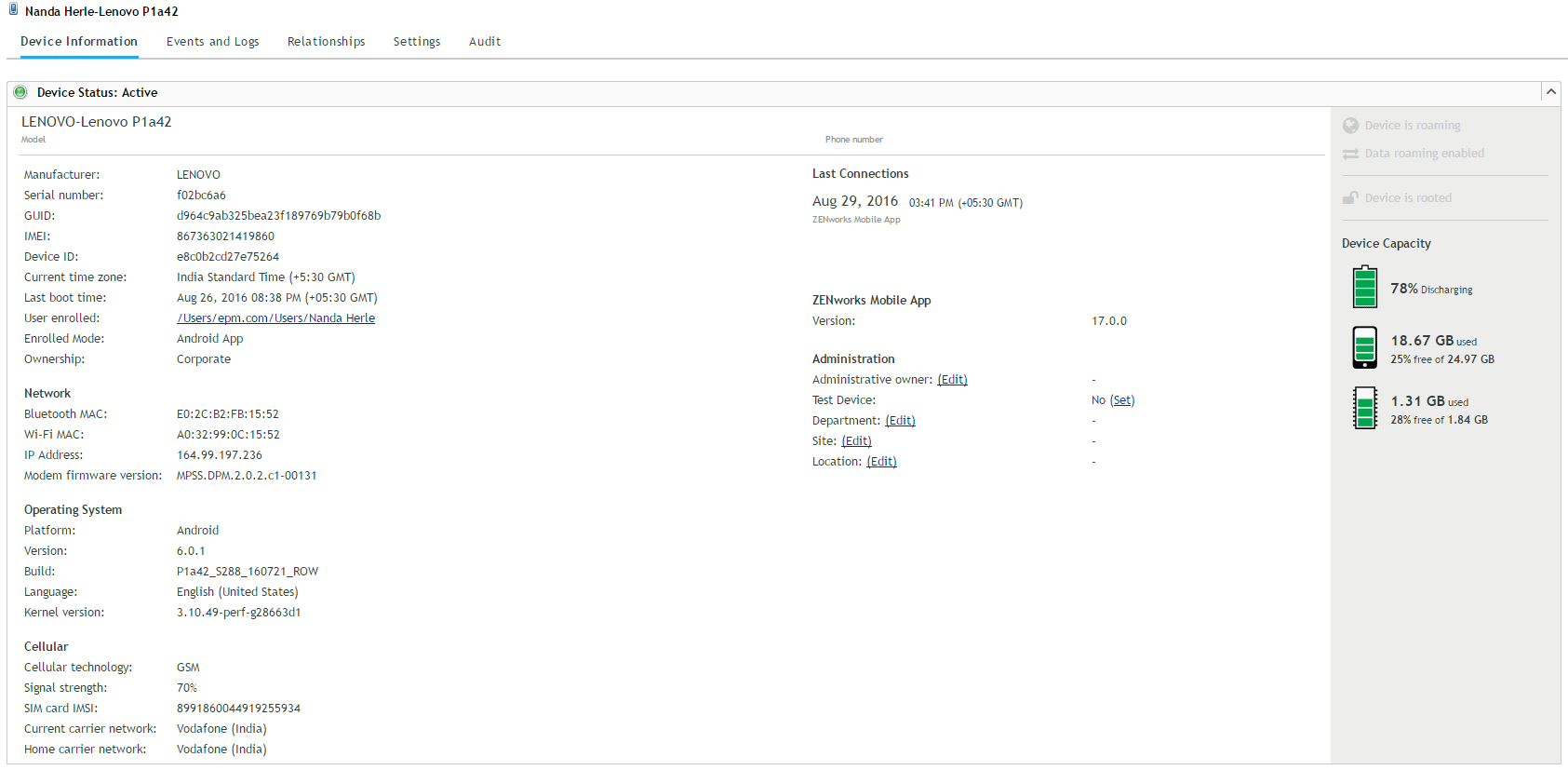
For instance, there is a common device listing as shown in figure 1. But when compared to the information display for a non-mobile device, the information display for a mobile device provides mobile-specific information in a better, more meaningful way (figure 2).
Managing email
Email can be considered the lifeline of most organisations. Providing, and then subsequently managing, email access to users on the move remains the most important task for many organisations. ZENworks 2017 provides two main configurations to make this happen:
- Configure ZENworks to front-end an organisation’s mail servers – In this configuration, all mail flows securely through ZENworks servers and is delivered to end users. With this configuration, it is possible to manage devices through the mail application on a user’s device without the need for a separate application.
- Configure mail to flow directly from the e-mail server – In this configuration, ZENworks is used to configure the email profile on a supported device but doesn’t become the gateway for accessing the mail.
And the best part? This distinction need not be enforced at the organisation level, but can be configured per user!
Configuration of email is quite simple and essentially consists of 2 steps:
- ActiveSync Configuration – IT administrators link their Active Sync servers to ZENworks through an easy to use configuration wizard. Once linked, ZENworks front-ends the ActiveSync server and deliver email to client devices.
- Email Policy – Through a policy, IT administrators define email settings. Once defined, the email policy is assigned to users or devices, allowing the assigned users or devices access to email.Securing mobile devices
Securing mobile devices is one of the most important reasons for having an UEM solution. If you are going to allow users to receive email and other types of content, you want to protect that data and possibly that device. With ZENworks 2017, securing mobile devices is as simple as creating a set of policies and assigning them to users or devices. ZENworks 2017 provides two different types of policies:
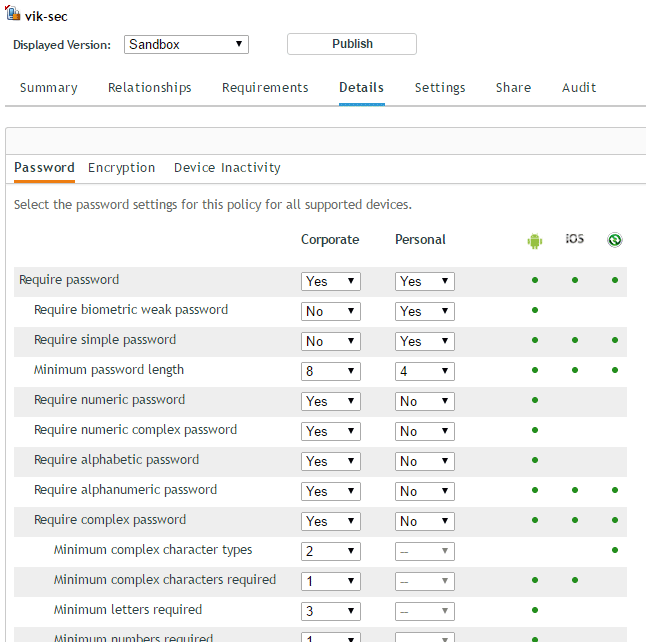
- Security Policy – Enables an IT administrator to secure a mobile device by enforcing a password on the device. This policy provides various password options ranging from a numeric password to a complex password consisting of different permutations of letters or numbers. The policy is platform agnostic, allowing one policy to define password restrictions across multiple mobile platforms. Only the policy settings relevant to the platform are enforced (figure 3).
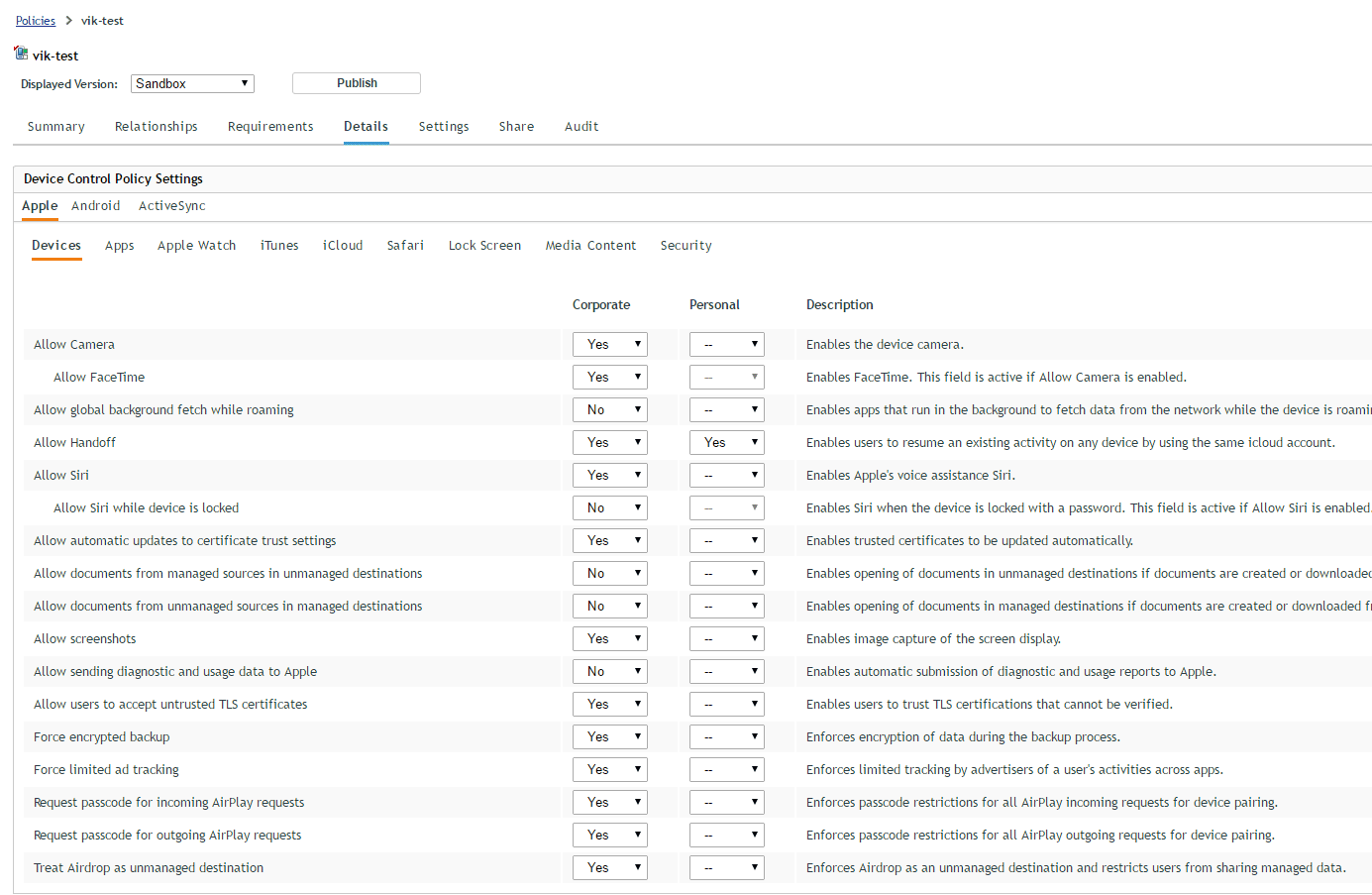
- Device Control Policy – Enables an IT administrator to define what capabilities of a device are available to a user and to what extent. For example, an administrator could use this policy to turn off the camera or Bluetooth communication. An IT administrator need not identify whether or not a user has a mobile device. All the administrator needs to do is create a policy group consisting of both mobile and non-mobile policies and assign the policy group to users. Regardless of the device (mobile or non-mobile) being used, the user is secure because the appropriate policies are assigned to the device. Apart from policies, there are other ways to ensure that a device and its data remains secure. ZENworks 2017 extends the existing Quick Task framework for this purpose. An IT administrator can simply select a mobile device and perform an appropriate quick task to secure the device.
- Lock / Unlock the device –If a device is lost, an IT administrator can remotely lock the device. If the user has forgotten the password, an administrator can remotely unlock the device.
- Wipe the device – If a device is lost or if a user is no longer a part of the organisation, an administrator can remotely wipe a managed device. Depending on the situation, an IT administrator can choose to selectively wipe the device ensuring that only corporate data is removed or to fully wipe the device by doing a remote factory reset.
Deploying applications
Securely deploying applications to mobile devices is one of the most used capabilities of an UEM solution. ZENworks has always been known for the robustness of its application management. ZENworks 2017 builds on this strength by providing a simple but familiar way to deploy applications to mobile devices.
Using the existing bundle creation workflow, an administrator can search for applications within an application store and then create a bundle containing the application. This bundle (figure 5) can be assigned to a device or user. Once assigned, the system deploys the bundle to a user’s device and installs the application. With ZENworks 2017, application deployment is initially available only for iOS. Support for other platforms is coming in the next set of releases.
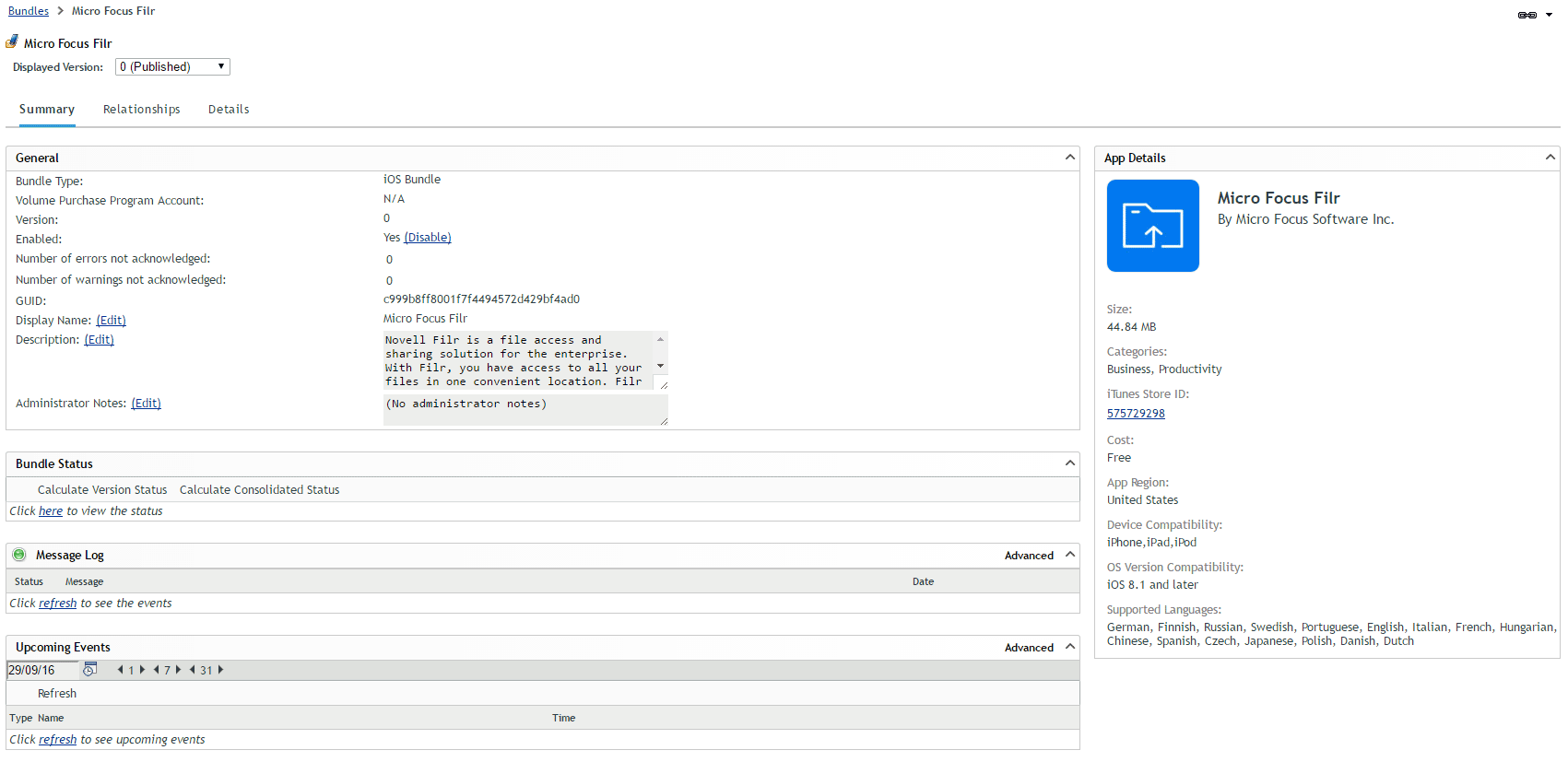
Apple’s Volume Purchase Program
For business and education users, the Apple Volume Purchase Program (VPP) provides an easy and convenient way to purchase applications and distribute them to mobile devices. ZENworks 2017 fully supports VPP:
- Configuration – Through an easy step-by-step setup wizard, IT administrators can link ZENworks to their Apple VPP account. After this link is established, ZENworks syncs to Apple and retrieves details about all the apps which have been purchased.
- App Deployment – After app details have been retrieved, ZENworks can create bundles out of them. The bundles can then be deployed just like any other mobile application deployment. As the bundle is using apps created via VPP, the license for the application is also automatically distributed by ZENworks.
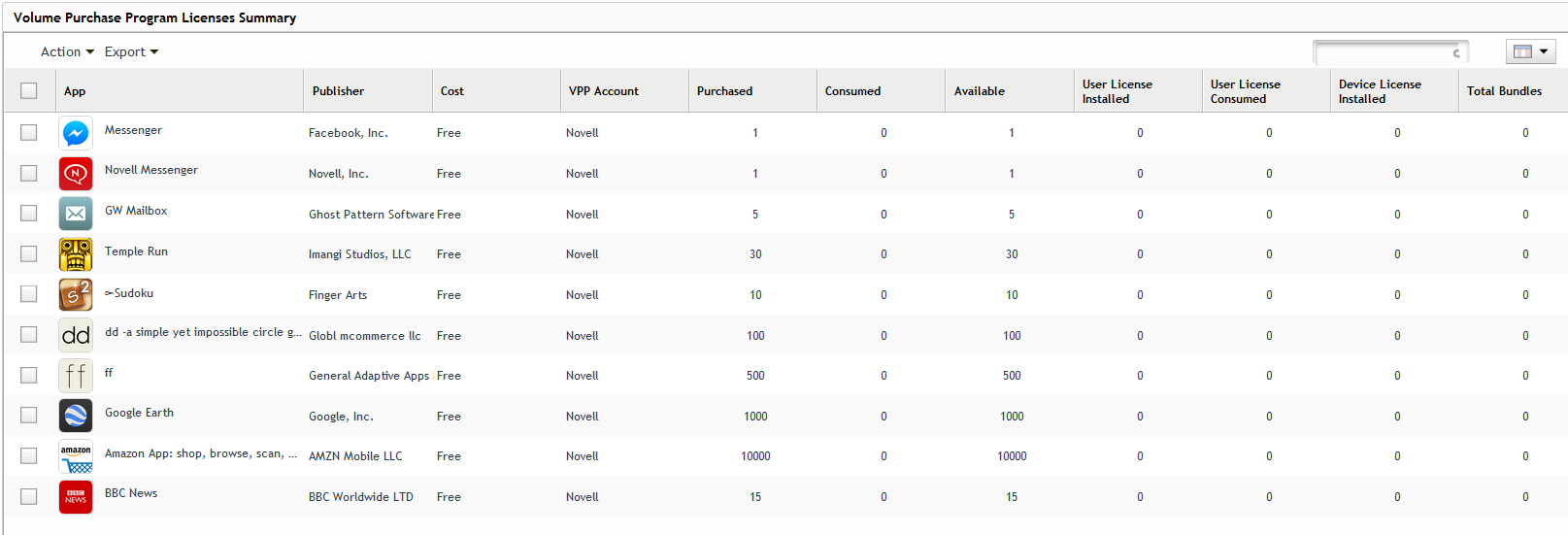
- License Tracking - While deploying, ZENworks keeps track of license consumption. A summary screen makes it possible to look up license consumption details for any purchased app.
Additionally, through an automated set of processes, ZENworks ensures that user enrollment to VPP happens in an automated manner without an IT administrator’s intervention. Also, the license counts are kept up to date by a set of processes that periodically scan for application installations and un-installations.
Looking forward
I’ve covered just a few of the many features coming in ZENworks 2017. Here at Micro Focus, ZENworks 2017 is only the first step on our journey towards achieving UEM greatness. To ensure that we run and not walk, we have changed our update framework and internal processes so that we can deliver updates at a much faster rate than previously, with the same high quality you’ve come to expect. With each update, we plan to add additional management capabilities and to support additional platforms.
From this vantage point, I don’t hesitate to proclaim that true Unified Endpoint Management starts NOW with ZENworks 2017! And we at Micro Focus invite you to join us in this journey.
This article was first published in OHM35, 2016/4, p5-8