In today’s world, nearly 40 percent of data breach and data loss incidents are caused by employees (insiders) through intentional or unintentional misuse of excessive privileges that they hold on critical systems in organisations. These employees can be Database Administrators, Super-users of operating systems or Domains, Data Centre Administrators, contract workers and so on.
By looking at the trends of these incidents over past few years there is a real need for enforcing the least-privilege principle, by limiting insiders’ initial access to just what they need along with enforcing access controls when using privilege elevation. The administrative activity on these critical systems should to be monitored, analysed for risks and actions taken instantly when a risky activity is found.
Micro Focus provides Privileged Account Manager in order to deal with the misuse of insider privileges. It enables organisations to monitor and control access to a wide variety of operating systems, databases, network devices, cloud services and applications.
Key Features of Privileged Account Manager (PAM)
Enterprise Credential Vault
The administrative credentials of critical systems are stored in PAM’s Enterprise Credential Vault, which protects them with multi-layered encryption. This vault can be a database created locally in PAM or any supported LDAP Server such as Active Directory or eDirectory.
If an employee has a need to fetch the credentials to a critical system or application and is authorised, the employee can request these stored credentials for a limited duration through Password Checkout, to gain privileged access to a critical system.
When the employee Checks-in the credential or if Checkout request duration is over, PAM resets the credential on the target system to avoid further usage of that credential. PAM audits the Password Checkout and Check-in activities as well.
PAM also uses these stored credentials in Single Sign-On scenarios, whenever an employee’s privileges need to be elevated in authorised sessions to target systems.
Privilege Elevation
PAM is capable of handling session initiation requests to target systems from authorised employees. It injects the stored privileged credentials into the authorised sessions, to elevate the privileges of the employees temporarily or on the basis of need.
For example, an employee Bob, who does not have any privileged access on a Windows Server can be elevated to an Administrator when the RDP connection is made from the PAM User Access console or Credential Provider. PAM constantly monitors and analyses the risks in these activities performed in these elevated sessions. The injected privileged credentials are hidden from the employee, to avoid the misuse of these credentials outside of PAM.
Privilege Elevation helps organisations to enforce the least-privilege principle for all the employees on all critical systems.
Centralised Policy Management
PAM provides a Command Control console to create access control policies based on the following criteria:
- Who - which employee (user)
- Where - on which system (Target System such as Windows Server, Linux Server, Database etc.)
- What - type of access or command (RDP, SSH, Telnet, Database Access, etc.)
- When - at what time (Weekday and Time)
- How - which level of Access (Administrative, root, DBA)
It is also possible to add Perl scripts to these policies to add custom logic for authorising the employee based on any other criteria.
For example, if a token needs to be delivered to an employee’s email and the employee has to authorise against it to gain access, a customised Perl script to send the email and validate can be added to the policy.
Centralised policy management helps administrators to enforce the access controls on access to target systems in a simpler way and almost instantaneously. A simple drag and drop or a few button clicks are sufficient to assign or completely revoke an employee’s privileged access in an organisation.
Methods to connect to Target Systems
Agent-based: PAM Agent supports following modes on the supported operating systems when installed on the target system.
Windows OS:
- The PAM Agent must be installed on the Windows operating system in order to control and monitor the employees’ activity.
- Credential Provider – Enables employees to connect from the Credential Provider using their own credentials and elevate their privileges on RDP sessions seamlessly.
- RDP Relay – Enables employees to connect from the PAM User Console in a browser, using their own credentials and elevate their privileges on RDP sessions seamlessly.
- Run as Privileged User – Enables employees to elevate their privileges for a specific application even when they have connected to the RDP session using their own credentials.
- Direct RDP – Enables Admins to connect directly to the critical servers.
Linux/UNIX OS:
- Privileged Shell – Enables employees to connect remotely using any SSH Client using their own credentials and elevate their privileges seamlessly.
- Agent-less: This is relevant when the PAM Agent cannot or need not be installed on the target system.
SSH Servers:
- SSH Relay – Enables employees to connect to target SSH Servers running on any operating system or network devices and elevate their privileges on the SSH session seamlessly. It is possible to use SSH Relay from both the PAM User Console in browser or any SSH Client. It also enables the employees to use X11 over SSH Relay.
Database:
- Database Relay – Enables employees to connect to various databases without the need for installing the PAM Agent on either the Database Server or Client systems. Employees need to checkout credentials from the Credential Vault and they can use any database client when connecting through PAM DB Relay.
Remote Application SSO (using RDS):
- This is a newly introduced feature in PAM 3.5. It enables employees to connect to any Windows-based, Web-based or Java application with seamless privilege elevation.
Session Recording and Auditing
Employee activities in PAM authorised sessions are recorded and monitored constantly for risks. This recorded activity is stored in PAM Audit Managers in various formats.
Agent-based:
- Windows OS and Remote Applications (RDS) – Videos and System call audits.
- Linux/UNIX OS – Command and System call audits.
Agent-less:
- SSH Servers – Command audits and Videos for X11.
- Databases – SQL Queries as Command audits.
- Applications and Databases – Password Checkout and Check in events.
PAM is capable of monitoring the risks in real-time through a Command Risk configuration. PAM instantly disconnects the sessions automatically, if a matching risky activity is found in the Employees’ on-going sessions to the critical systems.
In such scenarios, PAM is also capable of Auto-Blocking the users immediately to revoke their access in the organisation to avoid the similar or any other risky activity that may be performed on other critical systems.
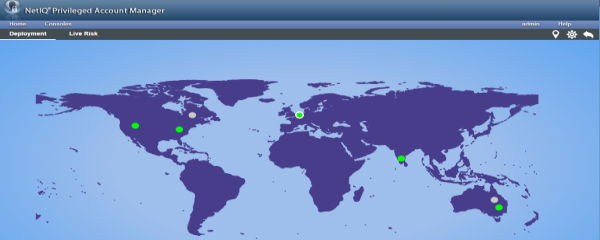
Deployment Dashboard
PAM provides various modules for the different functional services it provides. For example, the module for the policy engine is Command Control, the storage module for audits is Audit Manager and the module that stores the Credentials is the Enterprise Credential Vault.
The PAM Administrator can choose to install all or any of these modules in any geographical location depending on the need of proximity, high availability and fail-over requirements.
As PAM is modular in terms of installation and maintenance, the Deployment dashboard helps PAM Administrators to analyse the state (Primary/Backup) and the status (Online/Offline) of various modules installed in various geographical locations in a single view (see fig 1).
The Deployment Dashboard also shows the risky activities occurring in the entire PAM Deployment instantly, so that PAM Administrators can take necessary actions to remediate situation immediately.
Sniffer Tool
The PAM Sniffer Tool helps to discover the administrative accounts in LDAP Servers such as Active Directory and eDirectory; Operating systems such as Windows OS, Linux, and UNIX etc. It assists in creating an overview of all the administrative privileges in the entire organisation and enforcing the least privilege model.
What’s New in Privileged Account Manager 3.5
PAM version 3.5 has been released recently and it includes some significant new functionality and integrations with other Micro Focus products.
Application Single Sign-On
PAM has been able to elevate a Windows RDP session based on the access rights of employees since version 3.2. Starting from 3.5 onwards, PAM also provides a Single Sign-On capability to specific applications published through Windows Remote Desktop Services (RDS).
PAM Administrators can granularly configure the access to specific applications, without the need for providing an entire elevated desktop. It supports Windows (Thick clients), Web and Java applications.
Application-to-Application Password Management (AAPM)
When an application needs to interact with other applications through automated scripts or jobs and if the target applications require authentication, the credentials are hard-coded in the calling scripts or jobs in most scenarios.
PAM provides a way to replace these hard-coded credentials with tokens. These tokens are helpful in identifying the applications in PAM through REST APIs and securely fetch the credentials only when the applications have to authenticate.
Database Monitoring and Password Checkout
PAM 3.2 can audit employee activity on databases such as Oracle and Microsoft SQL Server in the SQL Query format. The Command Risk configuration helps to filter the risky activities from SQL Queries and take necessary action such as Auto-Disconnecting and Auto-Blocking the employee from further access.
Starting from 3.5 onwards, PAM supports several other databases such as MySQL, Maria DB, Sybase, and PostgreSQL. PAM also provides Password Checkout capability out of the box for all these databases.
New User Console
PAM 3.5 provides a brand new user console for employees to access the authorised resources or applications. Employees can also request temporary access to the resources to which they do not already have access; Password Checkout to fetch the credentials for authorised databases, applications and manage the AAPM Tokens. (Please see Figure 2 on previous page).
New Access and Reports Console
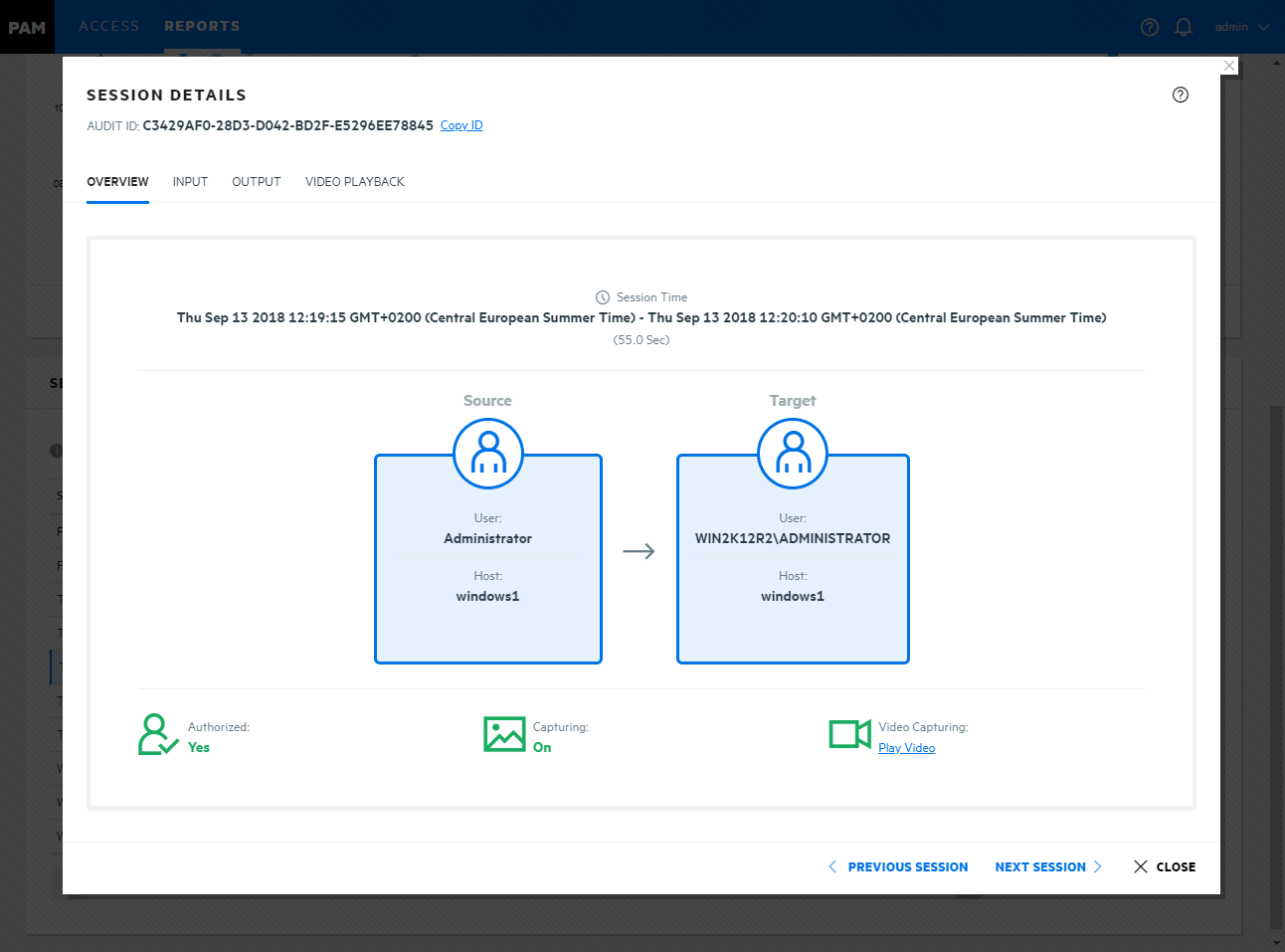
PAM 3.5 also provides a brand new Access and Reports console. These new consoles are part of the new User console itself, so the PAM Administrators can use this single console to access their authorised resources, manage the employee temporary access requests, manage Password Checkout requests and view recorded sessions. (Figures 3 and 4).
Integration with other Micro Focus Products
Identity Manager
PAM supports Automated User Provisioning with the help of Identity Manager and the IDM PAM Driver.
For example, employee rights assigned by PAM on target systems are revoked automatically when their Active Directory or eDirectory membership is removed.
Advanced Authentication
A wide variety of authentication methods such as TOTP, SMS, Smart Phone, etc. from Micro Focus Advanced Authentication, can be configured as secondary authentication methods in PAM.
Employees must authenticate successfully against all the configured authentication methods or chains before their privileges are elevated on target systems.
Sentinel
PAM can send the audited data to Sentinel (or any syslog server). Sentinel has a specific PAM Collector for parsing this data to create events. These events can be further analysed for threats using various correlation rules in Sentinel.
Conclusion
This short introduction to the features and functions of Micro Focus Privileged Account Manager show it is the best fit for many organisations spanning different technology domains in multiple countries due to its rich feature-set, flexibility, scalability, modularity, customisability and compliance with regulations.
This article was first published in OHM Issue 42, 2018/3, p15-18.