The volume of data, the sophistication of ubiquitous computing and the borderless flow of data are outpacing the ability to understand how personal data is being used. In this data-driven economy, consumers find it hard to trust companies for a variety of reasons when it comes to use of their personal data. For example, consumer reaction to data misuse can cause them to reduce their spending with a company by about one-third.1 Moreover, the number of cyber-attacks against enterprises and governments globally, continues to grow in frequency and severity. However, the findings in the Ponemon Institute Cyber Crime Study2 suggest companies using encryption technologies are more efficient in detecting and containing cyber-attacks.
This article briefly discusses how the fundamental encryption methods at the root of Micro Focus SecureData work and its application in two major business sectors.
A Unique Approach to End-to-End Encryption
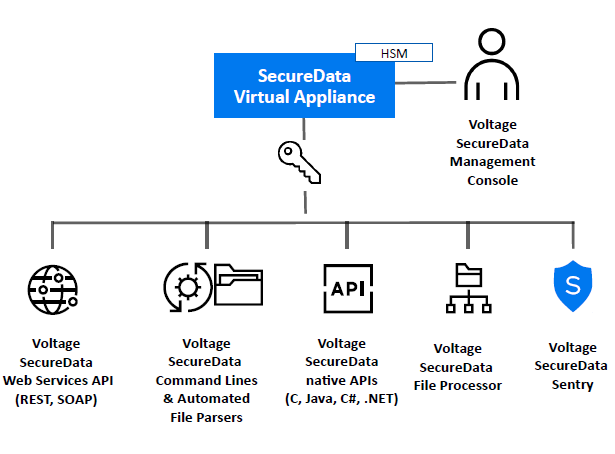
Voltage SecureData provides an end-to-end data-centric approach to enterprise data protection. It is a comprehensive data protection platform that enables you to protect data over its entire lifecycle—from the point at which it’s captured, throughout its movement across your extended enterprise, all without exposing live in-formation to high-risk, high-threat environments. The usability of data in its protected form is the essence of Voltage data protection. It opens access to data for use, without increasing risk of data exposure—and thus enables the enterprise to drive value from its data through analytics, and secure data sharing and portability.
Voltage SecureData permits data encryption, masking, tokenization, and other techniques without changes to data format or integrity, and with its stateless key management, eliminates the cost and complexity of issuing and managing certificates and symmetric keys (Figure 1). As a result, leading companies in financial services, insurance, retail, healthcare, energy, transportation, telecoms and other industries have achieved end-to-end data protection across hundreds of applications, because of the minimum, in most cases zero, impact to database schema and business processes.
Most applications can operate without change, using protected data. Voltage SecureData can easily be used with virtually any system, ranging from decades-old custom applications and mission-critical platforms to the latest enterprise programs and systems.
Any enterprise handling EU residents’ data needs to revisit the meaning of personal data due to GDPR’s expanded definition of personal data. Personal data includes name, location data, online id, genetic factors, etc. When an enterprise collects sensitive data, personally identifiable information (PII), payment card industry (PCI), or protected health information (PHI), it must secure and protect that data. Enterprises face significant financial penalties for non-compliance.
While GDPR sets a standard for data privacy worldwide, Voltage SecureData also protects information to help address compliance with PCI DSS, CCPA, HIPAA, and a host of industry, state and national data privacy regulations. Voltage SecureData is also compatible with the more stringent PCI DSS 3.2’s new requirements on transport encryption.
Hyper FPE: Encryption and Masking
Traditional encryption approaches, such as AES CBC, have enormous impact on data structures, schemas and applications. Instead Hyper FPE is NIST-standard using FF1 mode of the Advanced Encryption Standard (AES) algorithm, which encrypts sensitive data while preserving its original format without sacrificing encryption strength. Structured data, such as Social Security number, Tax ID number, credit card, account, date of birth, salary fields, or email addresses can be encrypted in place. Traditional encryption methods significantly alter the original format of data.

For example, a 16-digit credit card number encrypted with AES produces a long alphanumeric string. As a result, database schema changes are required to facilitate this incompatible format. Hyper FPE maintains the format of the data being encrypted so no database schema changes and minimal application changes are required—in many cases only the trusted applications that need to see the clear data need a single line of code.
Tools for bulk encryption facilitate rapid de-identification of large amounts of sensitive data in files and databases. Typically, whole systems can be rapidly protected in just days at a significantly reduced cost.
In fact, Hyper FPE allows accelerated encryption performance aligning to the high volume needs of next generation Big Data, cloud and Internet of Things, and supports virtually unlimited data types. Hyper FPE de-identifies production data and creates structurally valid test data so developers or users can perform QA or conduct data analysis—all without exposing sensitive data. The Voltage SecureData management console enables easy control of policy and provides audit capabilities across the data life cycle.
Stateless Key Management
Stateless Key Management securely derives keys on-the-fly as required by an application, once that application and its users have been properly authenticated and authorised against a centrally managed policy. Advanced policy controlled caching maximises performance. Stateless Key Management reduces IT costs and eases the administrative burden not least by eliminating the need for a key database.
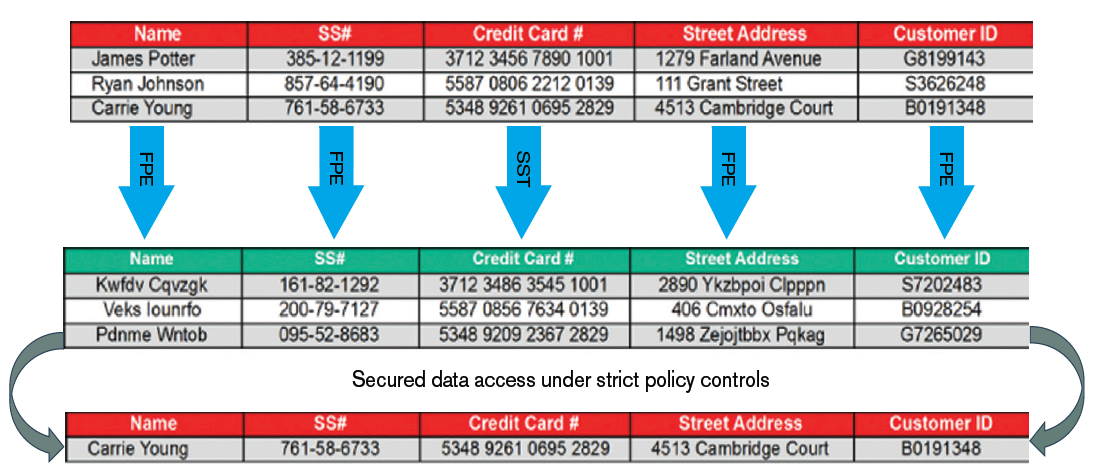
Hyper Secure Stateless Tokenization (SST)
Hyper SST is offered as part of the Voltage SecureData platform and is an advanced, patented, data security solution that provides enterprises, merchants, and payment processors with a new approach to help assure protection for payment card data. Hyper SST is “stateless” because it eliminates the token database, which is central to other tokenization solutions, and removes the need for storage of cardholder or other sensitive data.
Hyper SST uses a set of static, pre-generated tables containing random numbers created using a FIPS random number generator. These static tables reside on virtual “appliances”—commodity servers—and are used to consistently produce a unique, random token for each clear text Primary Account Number (PAN) input, resulting in a token that has no relationship to the original PAN.
Case study 1: Automotive industry
 Auto manufacturers capture massive volumes of data that, with predictive analytics, can produce valuable insights to monetise, and improve products, operations, and better serve customers with new features. For example, connected cars can now report their health status to get ahead of maintenance and keep customers safer! Sensor data can be packaged and sold to transportation agencies and cities to aid in traffic design, road maintenance, and other initiatives.
Auto manufacturers capture massive volumes of data that, with predictive analytics, can produce valuable insights to monetise, and improve products, operations, and better serve customers with new features. For example, connected cars can now report their health status to get ahead of maintenance and keep customers safer! Sensor data can be packaged and sold to transportation agencies and cities to aid in traffic design, road maintenance, and other initiatives.
Auto IoT (connected cars) is one of the most important and fastest growing sub-sectors of consumer IoT, and is expected to generate significant value to users, companies, and whole economies.3 With data pouring in around the clock from millions of cars on the road, auto companies are implementing data lakes and high performance analytic platforms to capture and use real-time sensor data and other traffic, combined with historic data.
Keeping this sensitive data secure and private for use in analytics is a major challenge. According to the Upstream Security Automotive Cybersecurity Report 2019, there was a 6 fold increase in automotive cyberattacks between 2010 and 2018. These cyberattacks are impacting every aspect of the sector from Tier 1 companies to OEMs, fleets, car rental, insurance companies, and more.
Security is the top barrier to IoT adoption across industries, but the connected car market is soaring, promising a continued explosion in data volumes—and risk. The undeniable benefits of IoT are dangerously offset with the heightened risk of data breach and potential loss of data privacy that will certainly spell trouble in the form of fines and penalties in an increasingly regulated industry, not to mention the associated losses related to brand damage.
While there are many areas of risky data exposure in the automotive IoT ecosystem, there’s no question that the back-end data lake presents a major target for cyber-attackers. With this realisation, there’s potential organisational conflict between creating new value with open access to data for analytics against securing data in a locked-down, unusable mode, to limit liability of misuse.
Using data at scale while lowering risk requires protection that scales with the data. This calls for de-identifying data as close as possible to its source before ingestion into analytics platforms and data lakes. This can be a powerful method to eliminate gaps in protection, masking the sensitive data elements with usable, yet de-identified surrogate values that maintain format, behaviour, and meaning. Yes, the answer is Voltage Hyper Format-Preserving Encryption (FPE) which preserves the characteristics of the original data, including numbers, symbols, letters, and numeric relationships that maintain referential integrity across distributed data sets.
To address data privacy compliance for its customers, while enabling safe analytics on IoT-generated data in their data lake, one major auto manufacturer is using Voltage Hyper FPE to protect in-car sensor data, Vehicle Identification Numbers and geo-location data streaming from customers’ cars. The data is used for multiple purposes, including vehicle quality control. Engineers look at sensor data to identify potential problems in specific components or groups of vehicles, while data scientists run thousands of reports against vehicle data for internal research purposes. This auto-maker’s volumes of real-time data are predicted to grow to around 20 petabytes, in the near-term, for these use cases.
Case study 2: Telecommunications
 Data is central to the telecoms business where value is created with massive volumes of messages and data records pouring in around the clock. Telecommunications service providers (telcos) are implementing data lakes to capture real-time traffic combined with historic data. Telcos are streaming, feeding, and storing sensitive data including IMEI, IMSI, tower data, and CPNI that must be protected.
Data is central to the telecoms business where value is created with massive volumes of messages and data records pouring in around the clock. Telecommunications service providers (telcos) are implementing data lakes to capture real-time traffic combined with historic data. Telcos are streaming, feeding, and storing sensitive data including IMEI, IMSI, tower data, and CPNI that must be protected.
For example, a network of 100 million customers may generate more than 35 billion CDRs (Call Detail Records) per day4, which if compromised can lead to loss of customer confidence and regulatory penalties. There is much at stake if no clear data protection strategy is in place.
One large multi-country telco runs back-bone infrastructure that delivers services to over 300 million consumers. With the rise in threats from criminal and nation-state sponsored cyber-attacks, and government mandates to protect critical infrastructure, the company embarked on a new mission. The goal was to ensure that all sensitive data would be protected wherever it moves across all systems, applications and services.
Today, that top-down vision is achieved with petabytes of data secured across 26 data types, thousands of applications, in the data lake and cloud workloads. Voltage SecureData technology is the new standard at the company. The deployment protects data for billions of transactions and mobile devices, while enabling IoT strategies to capture new market segments, and sustain growth and innovation.
The challenges of using data for innovation are two-fold:
- Threats and attack vectors have multiplied
- It is no surprise that states, regions and industries are regulating data privacy where companies fail to do so. It creates a challenge. The challenge posed to IT and InfoSec professionals is how to support and enable innovation in the enterprise without increasing risk of data exposure and data privacy non-compliance.
A common reaction is to ingest as much data as possible to gain better insights, but then lock down data access due to the risk. With that approach companies fail to get needed ROI from their technology investments. We’re conditioned to think of a technology like encryption as a tool to reduce risk, but not as a tool to help drive value. The problem is traditional security can’t protect data in use, nor enable data privacy at the same time. But Format-Preserving Encryption can protect data in use, in motion, and at rest.
While there are great complexities to addressing data privacy, a critical positive action enterprises can take now, to make progress, is to protect sensitive data at the data level, to enable persistent protection that travels with the data wherever it is. Voltage SecureData is an innovative, new approach—already proven in the highest performance analytics environments across hybrid IT in multiple business sectors.
References
- www.microfocus.com/media/flyer/scalability_of_big_data_security_for_telcos_flyer.pdf
- https://community.softwaregrp.com/t5/Security-Blog/For-Auto-Makers-Data-is-the-new-fuel-for-Analytics-and-/ba-p/1684690?utm_campaign=00164297
- Bridging the Trust Gap in Personal Data, BCG, March 2018
- 2017 Cost of Cyber Crime study: Global Ponemon Institute, October 2017
- NDP Analytics, Interoperability and the Internet of Things, NDP Analytics, December 2017
- www.rcrwireless.com/20141014/big-data-analytics/telco-case-study-vodafone-argyle-data-tag62
This article was first published in OHM43, 2019.1, p17-20

