Domain Services for Windows (DSfW) is the only enterprise grade software in market that can substitute Active Directory for most authentication needs, or co-exist as an identity store in an AD environment with relative ease. While primary use cases for DSfW are well known, in this article we focus on the forest functional level upgrade to AD2012 level in OES 2018. Until now the functional level for DSfW domains was AD2003.
AD2012 schema and functional level
The functional level upgrade is basically updating some aspects of domain controllers that are part of your DSfW domain. It happens when all domain controllers install or upgrade to OES 2018 DSfW. The schema definition of various LDAP based object classes and attributes being the most prominent.
Additional definitions to this LDAP schema enable AD2012 specific applications to start working with DSfW (or makes them easier to integrate). msds-SupportedEncryptionTypes is one such widely used attribute. Overall, the number of definitions have increased from 2,876 in AD2003 level to 3,354 in AD2012 level. The upgrade also involves updating msds-BehaviorVersion attribute values to 5, so that Windows and other clients know the functional level of the server.
The screenshot in figure 1 of a mmc (launched in Windows10) connected to OES 2018 DSfW shows the Functional Upgrade.
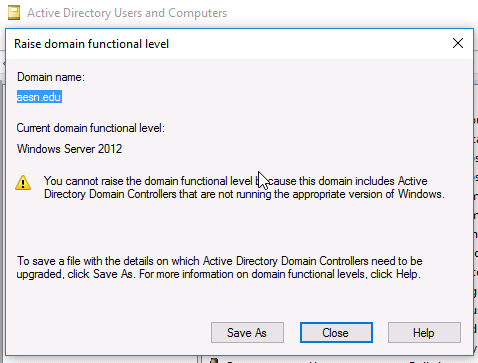
AES encryption
Two other prominent features are AES encryption and Fine Grained Password Policy. Prior to AES, Arcfour encryption was used. Being vector encryption makes AES more secure. The scope of the encryption involves mainly the Kerberos protocol. DCERPC and LDAP communications are also encrypted by AES. For many of these packets, encryption is at two levels, session and ticket level.
Fine grained password policy
Fine Grained Password Policy is a more customisable alternative to Account Policies supported by the AD2003 functional level. Single account policy is common to all users in the domain, and is configurable using the gpmc tool in mmc. With an upgraded functional level, a new type of policy, Fine Grained Password Policy is introduced.
Like the traditional password policy, we can define attributes such as:
- Password Length
- Complexity
- Duration
Unlike the traditional policy, it can be applied to individual users.
Administrators can use the ADSIEDIT tool for creating and associating the fine grained password policy. Reference 1 gives further details on exactly how it can be done.
Overall, fine grained policies can be used to devise stricter password policy rules for key users such as Finance Administartors.
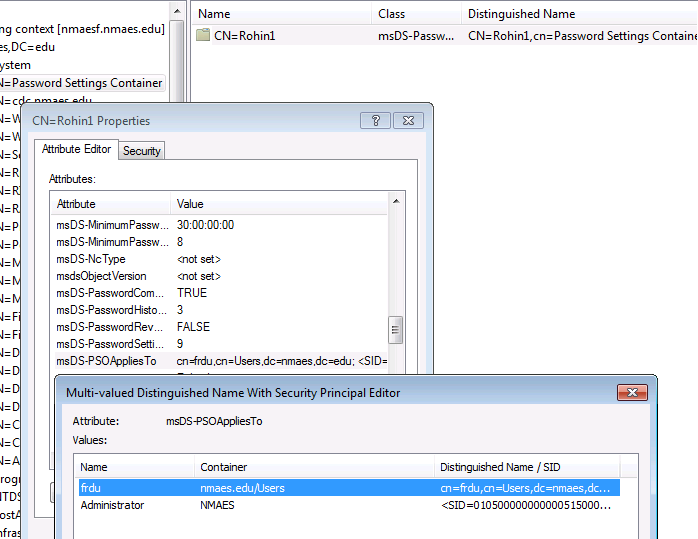
AD2008 policies validation
As part of the functional level upgrade, we also validated two key Group Policies introduced in AD2008. One involves disabling USB for workstations that are part of a domain, and have the Group Policy applied. The other is related to firewall settings for domain users or their subset. Such policies are quite useful for geographically distributed domains. Overall there are no code changes needed for AD2008 policies, they work out of the box for DSfW.
In summary
The functional level upgrades included by default with DSfW in OES 2018 makes it all the more easy to integrate 3rd party software with it. In the absence of this upgrade, a lot of custom work was involved in integrating newer versions of 3rd party software with DSfW.
Now, most of the latest versions of 3rd party software work out of the box or with minimal customisation.
By the way, this functionality has also been made available on top of OES 2015 SP1, but the capabilities were disabled by default and you need to explicitly enable them if needed.
Ref [1]: Fine Grained Password Policy Documentation - https://www.novell.com/documentation/oes2015/acc_dsfw_lx/data/b1qbowbm.html
This article was first published in Open Horizons magazine, Issue 39, 2017/4, p12-13.
....To view the full article you must have a full Digital Subscription.

